Targeted UAC-0102 cyber attacks against UKR.NET service users (CERT-UA#6858)
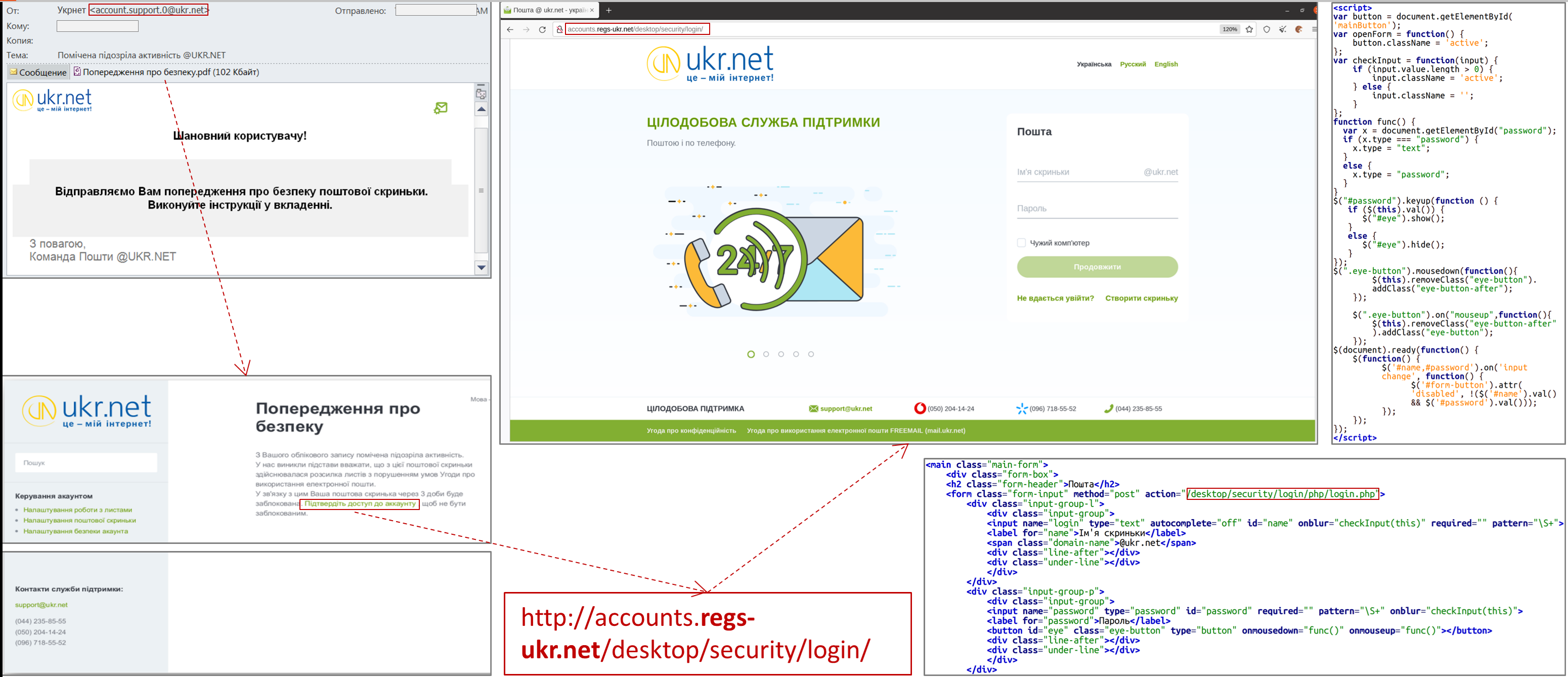
An e-mail was received from a participant of the information exchange with the subject "Suspicious activity observed @UKR.NET" and an attachment in the form of a PDF file "Security warning.pdf" sent, apparently, on behalf of UKR.NET technical support (sender's e-mail address: "account .support.0@ukr.net").
The mentioned PDF document contains a link to a fraudulent web resource that imitates the web page of the postal service.
In the case of authentication on a fake website, the user's login and password will be sent to attackers, which will create the conditions for unauthorized access to the user's e-mail box by third parties.
CERT-UA took additional measures to analyze the network infrastructure used to carry out similar cyber attacks from 2021, as a result of which at least 118 related domain names registered by the company "Internet Domain Service BS Corp." were discovered. (@internet.bs, Bahamas). According to Domaintools, the relevant servers are located in the Netherlands at the technical site "Nice-IT" aka "@as49447.net" (autonomous system number: 49447).
The described activity is tracked by the identifier UAC-0102.
In order to minimize the likelihood of cyber threats against citizens of Ukraine, the identified domain names were added to the DNS RPZ of the zone served by CERT-UA, and also transferred to CSIRT-NBU specialists for the purpose of adding the "fraud" zone to the DNS RPZ.
We urge UKR.NET users to use the standard functionality of the mail service and to immediately take measures to set up multi-factor authentication.
It is recommended, starting from 01.01.2023, to check the facts of network interaction with domain names and IP addresses specified in the "Cyber Threat Indicators" section, occasionally paying attention to the presence of unauthorized configured mail filters and third-party devices/applications that need access to the mailbox.